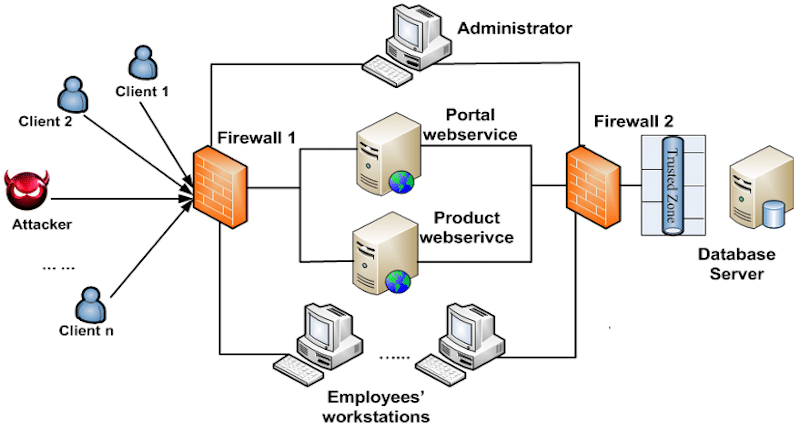
Modern-day attackers tend to use sophisticated multi-stage/multi-host attack techniques and anti-forensics tools to cover their attack traces. Due to the current limitations of intrusion detection systems (IDS) and forensic analysis tools, the evidence can be a false positive or missing. Besides, the number of security events is so large that finding an attack pattern is like finding a needle in a haystack. Under this situation, reconstructing the attack scenario that can hold the attacker accountable for their crime is very challenging.
This paper describes a probabilistic model that applies Bayesian Network to constructed evidence graphs, systematically addressing how to resolve some of the above problems by detecting false positives, analyzing the reasons of the missing evidence and computing the probability for an entire attack scenario. The authors have also developed a software tool based on this model for network forensics analysis. Their system is based on a Prolog system using known vulnerability databases and an anti-forensics database that is similar to the NIST National Vulnerability Database (NVD). Their experimental results and case study show that such a system can be useful for constructing the most likely attack scenario and managing errors for network forensics analysis.
Use this link to read full article by Changwei Liu, Anoop Singhal and Duminda Wijesekera.