Mobile devices of Apple such as iPhones and iPads are 15% of the mobile market. Therefore, it is often on research in forensic laboratories.
In this article we will consider two key points of forensic analysis of such devices:
1) Extracting data from Apple mobile devices;
2) Forensic analysis of these data.
Extracting data from Apple mobile devices
There are four basic types of data extraction in mobile forensics:
- Logical extraction of the device retrieves only certain data (phonebook, call, SMS etc.). Typically, such extraction is performed by installing a special application on the mobile device. However, due to the organization of the memory of your mobile devices and safety for mobile Apple devices, this method is not applicable.
- Create a backup of the device retrieves all the logical data, the extraction of which is allowed by safety regulations. This is the most common method to extract data from mobile devices of Apple.
- The file system extraction – with this method, you can retrieve all data from the logical device. This method is applicable for Apple devices subjected to jailbreak . It allows you to extract the maximum amount of data from such devices. Unfortunately not all devices can be jailbroken. For example, the jailbreak can be done for Apple mobile devices with the latest version of the operating system ‘iOS’.
- Creating a physical dump using this method you can retrieve not only logic data, but also deleted files from the device. Unfortunately, in case of mobile Apple devices this method only works for iPhone 4 and older models.
For making iPhone forensic images (in case of iPad the process of creating a forensic image and analysis of data will be similar), use the free utility “Belkasoft Acquisition Tool.”
A free utility ‘Belkasoft Acquisition Tool’ and a trial version of the software ‘Belkasoft Evidence Center’ are available at http://belkasoft.com/get
Run the program, and click on the icon ‘Mobile device’ in the opened window.

Fig. 1. The main window of the program ‘Belkasoft Acquisition Tool’.
On the next window, click on the icon ‘Apple’.

Fig. 2. The window for selecting device type (‘Apple’ or ‘Android’).
Unlock the device from which you need to extract the data, connect it to the computer and, in response to the request on the screen of the device, click ‘Trust’. On the next window you must specify the path where the returned data will be stored and click ‘Next’.

Fig. 3. The window for connecting a mobile device.
The data extraction process starts. When the extraction is completed, a window with information about the extracted data will be displayed. You can go to the extracted data by clicking on the ‘Open target folder’ label in this window.

Fig. 4. The window with information about the performed extraction.
Analysis of extracted data
For the analysis of data retrieved one could use the software ‘Belkasoft Evidence Center’. Run the program. Define the parameters of the new case such as: name, path, where to place the data of the case, the name of the researcher (expert), case description, time zone. Click on the button ‘New case’.

Fig. 5. The window for setting up a new case.
On the next window, we specify the path to the data from the mobile device that was extracted earlier. Click the ‘Next’ button.

Fig. 6. The window for data source selection.
In the next window, specify the data types (chats, email messages images, videos, calls, SMS messages, etc.) that must be removed. The more data types are specified for extraction, the longer the analysis will be performed. However, for the analysis of mobile data, the analysis time is not critical. Thus, the analysis of the device used as an example took 12 minutes.

Fig. 7. The window for selecting data types to be found
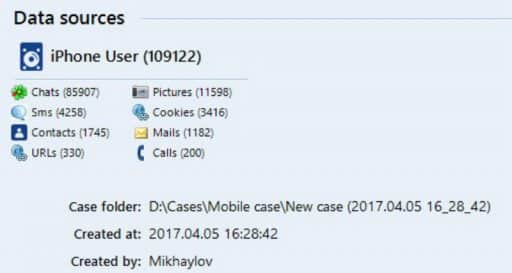
Upon completion of the analysis process, the detected data types will be displayed.

Fig. 8. Data extracted from the analyzed device.
Is it possible to recover deleted data from an iTunes backup. Yes. It is possible. ‘Belkasoft Evidence Center’ can recover deleted records of Phonebook, Calls, SMS messages, Web Browser History, etc.
Thumbnails can provide info about images and video files which were deleted on the investigated device.
The extracted and recovered data can be viewed and analyzed in the ‘Belkasoft Evidence Center’ program. Also, one can create forensic reports for them, which, including, can be presented as evidence in a court.
Conclusion
In this article, we looked at the types of data retrieval from mobile devices. An example of extracting and analyzing data extracted from the iPhone with the help of available programs, such as ‘Belkasoft Acquisition Tool’ and ‘Belkasoft Evidence Center’, is given.
Authors:





Comments are closed.