First of all I want to say this – my dear colleagues, the protection of accounts – albeit typical, but in any case not an easy task, especially for the average system administrator who is not a specialist in information security.
If an attacker has gained access to the list of accounts, it will be able to block them all. Here, in particular, should be aware of one thing – any account in the AD domain can send to the directory service, and the default has read almost all of its sections. In practice, this means that if an attacker knows the login password of at least one user, it is a simple-the LDAP query to get the list of all (yes, quite all) accounts in the domain.
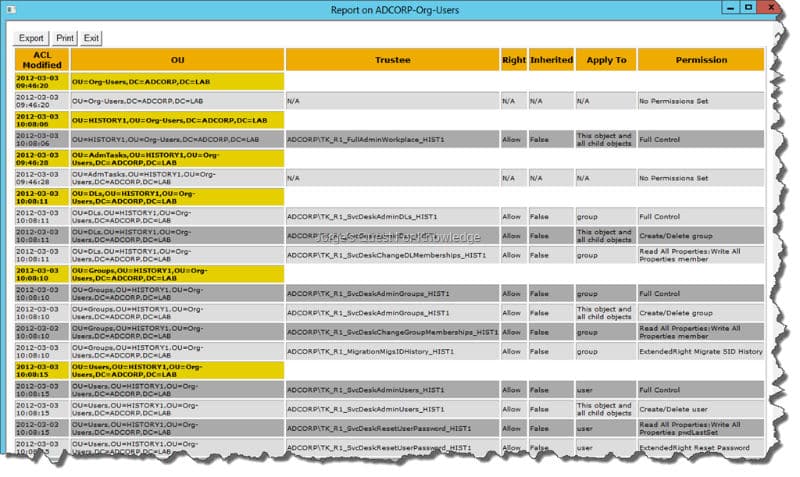
Often this service accounts receive privileges in Active Directory. It is important that these permissions are delegated to the principle of least privilege (POLP), since these service accounts, usually a security problem since its exposure and it’s probably never going to change, and may even have known password. Strong likelihood that some of these delegations are not valid AD and people left their function or even company, but still remained delegated authority.
With the permission for which is necessary to monitor you can read here. The key here is to know your delegation and your best tool RBAC! With a good model of RBAC model next level and using a good naming convention will be easier to detect bad delegation.