AXIOM is our one of the best tools. A few days ago Magnet Forensics has released AXIOM V2. Now AXIOM contains many features. We were especially delighted that the functional Volatility appeared in a new version of AXIOM. Volatility is the best tool for memory forensics. The combination of AXIOM and Volatility is clearly an excellent idea. And of course we immediately started testing this functionality.
The first thing the user sees in the main AXIOM window is adding the MEMORY button in the EVIDENCE SOURCES window.

If you click the MEMORY button, you will see the next EVIDENCE SOURCES screen with a single LOAD MEMORY DUMP FILE button.

It is not clear with what purpose this additional screen is made? Is this done to add the acquire memory dump button in the future? Setup file AXIOM has a size of more than 2GB. Therefore, it’s a bad idea to use AXIOM to create a memory dump. In addition, an examiner was offered two steps back to make a choice: LOAD EVIDENCE or ACQIURE EVIDENCE.
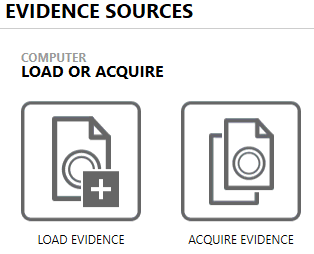
Okay. If you click the LOAD MEMORY DUMP FILE button, you will be prompted to choose a memory dump.

This is unusual, but AXIOM does not support memory dumps, which were created with FTK Imager. FTK Imager is a well-known and popular tool. And there is a version of FTK Imager Lite, which does not require installation.
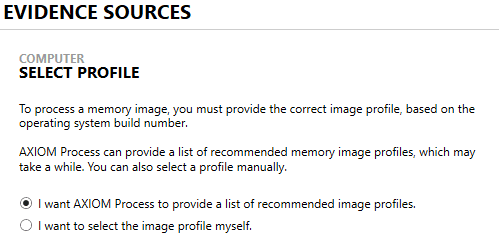
The next window prompts you to select the operating system profile. The profile can be detected automatically using AXIOM or can be selected manually from the list of available profiles.
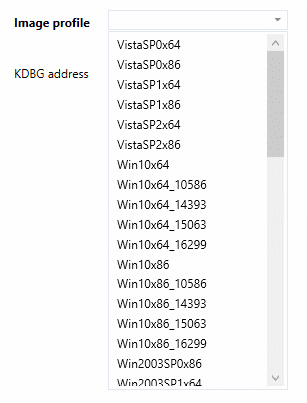
We opened Windows 10 Home memory dump (created with FTK Imager Lite) in AXIOM and waited for a long time for this tool to determine the profile of the operating system automatically. But it was unsuccessful. When we were tired of waiting, we canceled this process.
After that, we set the operating system profile manually and started the process of an analysis.
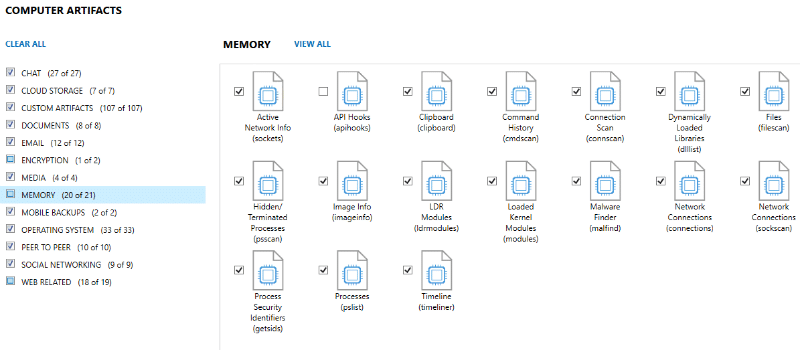
Categories of memory artifacts
After the analysis, you will see a new window of the AXIOM interface – Case dashboard.
In this window, there is a section called TOP ARTIFACT CATEGORIES. It is not clear why this is done. We can predict that the top category for memory dumps will always be Web Related. The operating System will always be the top category for Windows running PCs and laptops. Web Related or Chat will always be the top category for smartphones. Besides, the size of the top category is such that all other categories in the TOP ARTIFACT CATEGORIES section will not be informative.
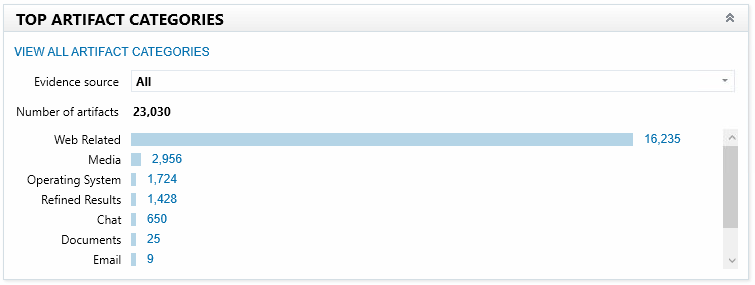
Categories of a memory dump
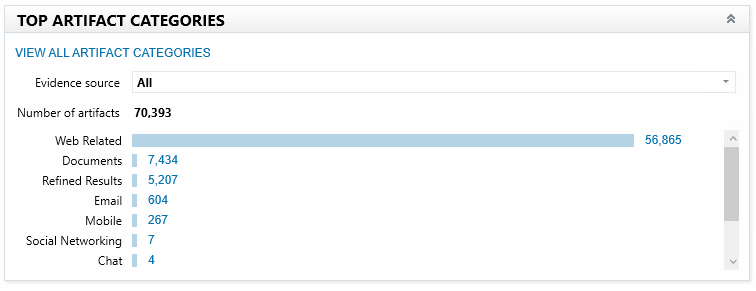
Categories of a full dump of an android smartphone
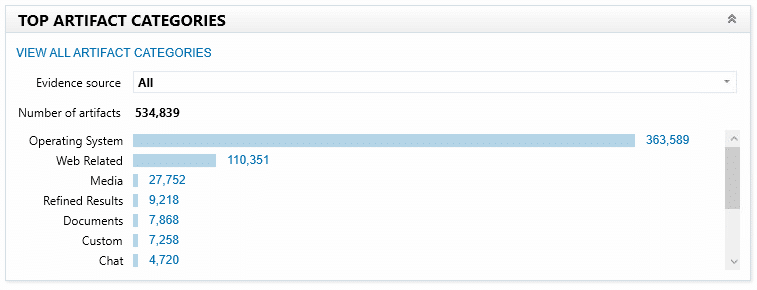
Categories of a Windows PC
If you click the inscription VIEW ALL ARTIFACT CATEGORIES, we get into the familiar interface of AXIOM Examiner.

In addition to the known artifacts in AXIOM Examiner, there is a new category MEMORY, which contains a lot of new information about the analysis of the memory dump such as Active Network Info, Connection Scan, Files, Processes, Dynamically Loaded Libraries, etc.
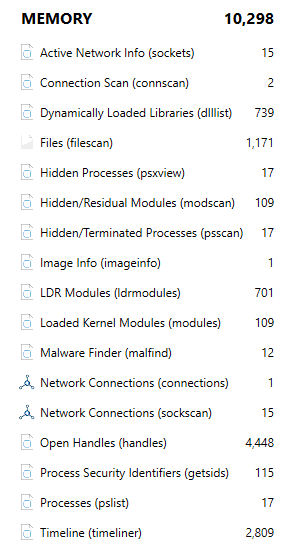
The most interesting category in this list is Malware Finder, which contains information about the files that can be pieces of malware.
Unfortunately, these files and suspicious processes cannot be extracted from the memory dump for additional analysis. We hope that this functionality will appear in the new versions of AXIOM.
Conclusion
As you can see, the new version of AXIOM has the functionality to explore memory dumps. Memory dumps can be created by Magnet Forensics free tool – Magnet RAM Capturer and other utilities. Now using AXIOM from a memory dump, we can extract not only familiar artifacts (such as: Web History, Chats, Emails, etc.) but also memory artifacts (such as Active Network Info, Connection Scan, Files, Processes, Dynamically Loaded Libraries, etc.).
Happy forensicating!
About the authors
Oleg Skulkin, GCFA, MCFE, ACE, is a DFIR enthusional (enthusiast + professional), Windows Forensics Cookbook and Practical Mobile Forensics co-author.
Igor Mikhaylov, MCFE, EnCE, ACE, OSFCE, is a digital forensic examiner with more than 20 years of experience and Mobile Forensics Cookbook author.






