Nowadays digital forensic labs have a few ways of extracting data from mobile devices. They are the following:
- logical extraction;
- backup extraction;
- file system extraction;
- Joint Test Action Group (JTAG) technique;
- Serial Peripheral Interface (SPI, ISP) technique;
- Chip-off technique;
- combined methods.
Chip-off is a technique based on chip extraction from a mobile device and reading data from it. This is the most difficult way of data extraction. But it must be used when all other methods failed. This method becomes more and more popular among mobile forensic examiners, so we decided to discuss this technique in details.
Hardware and software
There are a lot of tools for extraction chips from circuit boards; we’ll describe only a few.
Chip unsoldering
For chip unsoldering you will need an IR station. It’s difficult to name the model, because lots of them have the same features.
Data extraction equipment
Chips in mobile devices (eMMC) have interface similar to SD cards (but eMMC has 8 bit data bus, SD card – maximum 4 bit). All eMMC can work on 1 bit bus. But if we use this feature for data extraction, it will take too much time. So we need same equipment as for SD cards and also adapters for chips.
Hardware
- VISUAL NAND RECONSTRUCTOR [1]. This tool is very interesting, because Rusolut did a research and found the main types of BGA chips used in smartphones. Then they developed a series of adapters called SMARTPHONE KIT, which included adapters for such chips. This equipment is very useful – it reduces manual work greatly and allows an examiner to extract data from standard BGA chips very fast. We recommend to buy VISUAL NAND RECONSTRUCTOR with STANDART KIT and SMARTPHONE KIT adapters. Also Rusolut has a great knowledge base with solutions on extracting data from chips, which is available for registered users, and also articles and documentation available for free at their website [2].

Figure 1. VISUAL NAND RECONTRUCTOR (Rusolut) and adapters [3]
- ACE Lab equipment. ACE Lab developed PC 3000 Flash [4], which can be used for extracting data from BGA chips. You’ll get adapter kit for BGA chips with this tool.
ACE Lab also has great knowledge base available for registered users. It’s very useful.
- Adapter kits. You can find a lot of adapter kits for BGA chips at Aliexpress [5]. They are cheap, but you can alter data while using it. Also, there is no tech support.
Software
- One of the most powerful tools for chip-off dumps analysis is UFED Physical Analyzer [6]. This piece of software has lots of pre-made solution for parsing data. Also, an examiner can control the algorithm of data parsing choosing modules manually. What is more, you can write some code in Python for parsing data.
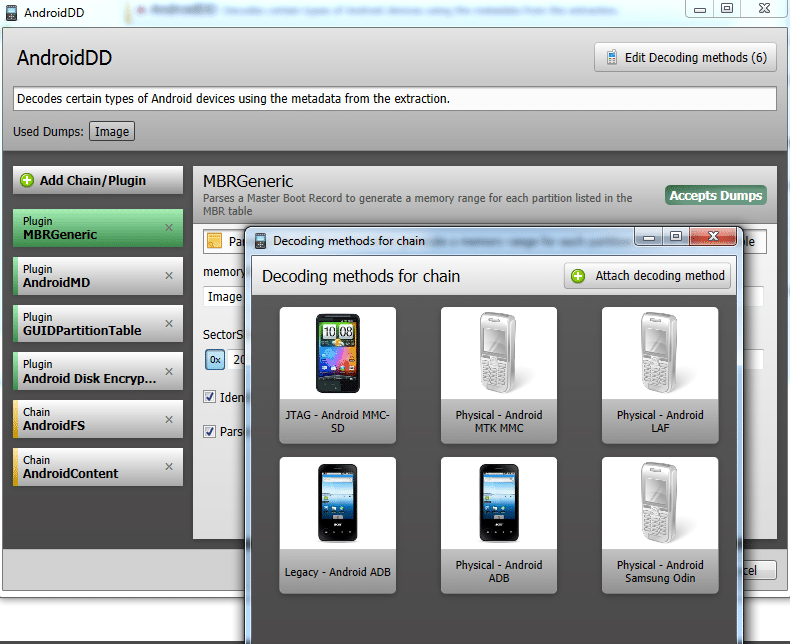
Figure 2. Customizing analysis chain of an Android smartphone dump
- XRY [7]. This tool has almost the same features as UFED Physical Analyzer: you can control parsing algorithm and you can write you own Python scripts.
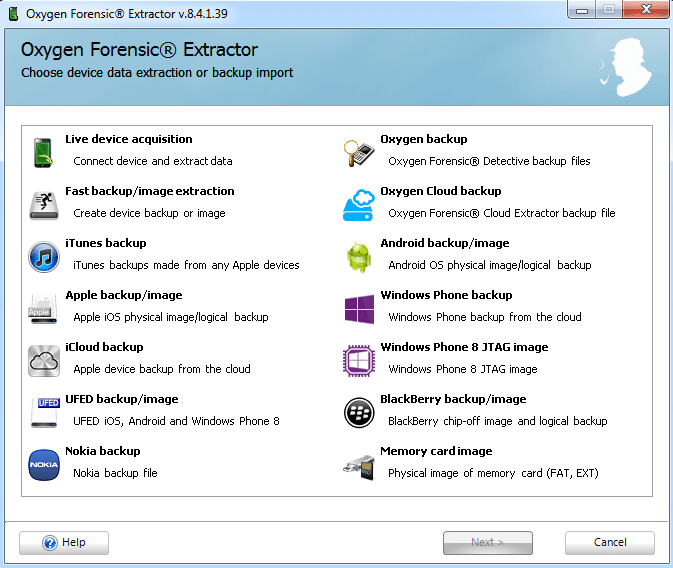
- Oxygen Forensics. This tool also has similar features. But it doesn’t allow you to control parsing algorithm. Why should an examiner use this piece of software? It has great tech support. We contacted them a few times having problems with parsing chip-off dumps – they created solutions for us very fast and gave it to us for free.
Figure 3. Oxygen Forensic Extractor (Oxygen Forensic Detective)
- Belkasoft Evidence Center [9]. The best thing about this piece of software – it supports extraction from lots of mobile apps. So, if you need to recover chats – this tool is for you. Also, Belkasoft is the first digital forensic company to support Windows Phone 8 dumps. Belkasoft supports data extraction from iOS, Android and Windows Mobile dumps.
- AXIOM (Magnet Forensics) [10] has features similar to Belkasoft Evidence Center.
- Autopsy [11] – extracts data from Android dumps. It’s very powerful tool. Also, it’s free.
Chip unsoldering: tips and tricks
Chip unsoldering is the most important part of chip-off process. The chip mustn’t be overheated. It will delete all data. Usually it happens, because an examiner thinks that air isn’t hot enough to melt soldering flux, and increases temperature too much. An examiner should remember, that chip is not only soldered to the board, but also glued with compound. That’s why you should not only heat it, but also try to extract it carefully. We recommend using IR station. Even the simplest IR station with automatic temperature regulator allows unsoldering BGA chips with safety. For standard chips unsoldering temperature is ~225-230 °C, for chips glued with compound – ~240-245 °C.
To extract a chip from a smartphone board we recommend heating it to 240 °C and then use a blade to extract it.
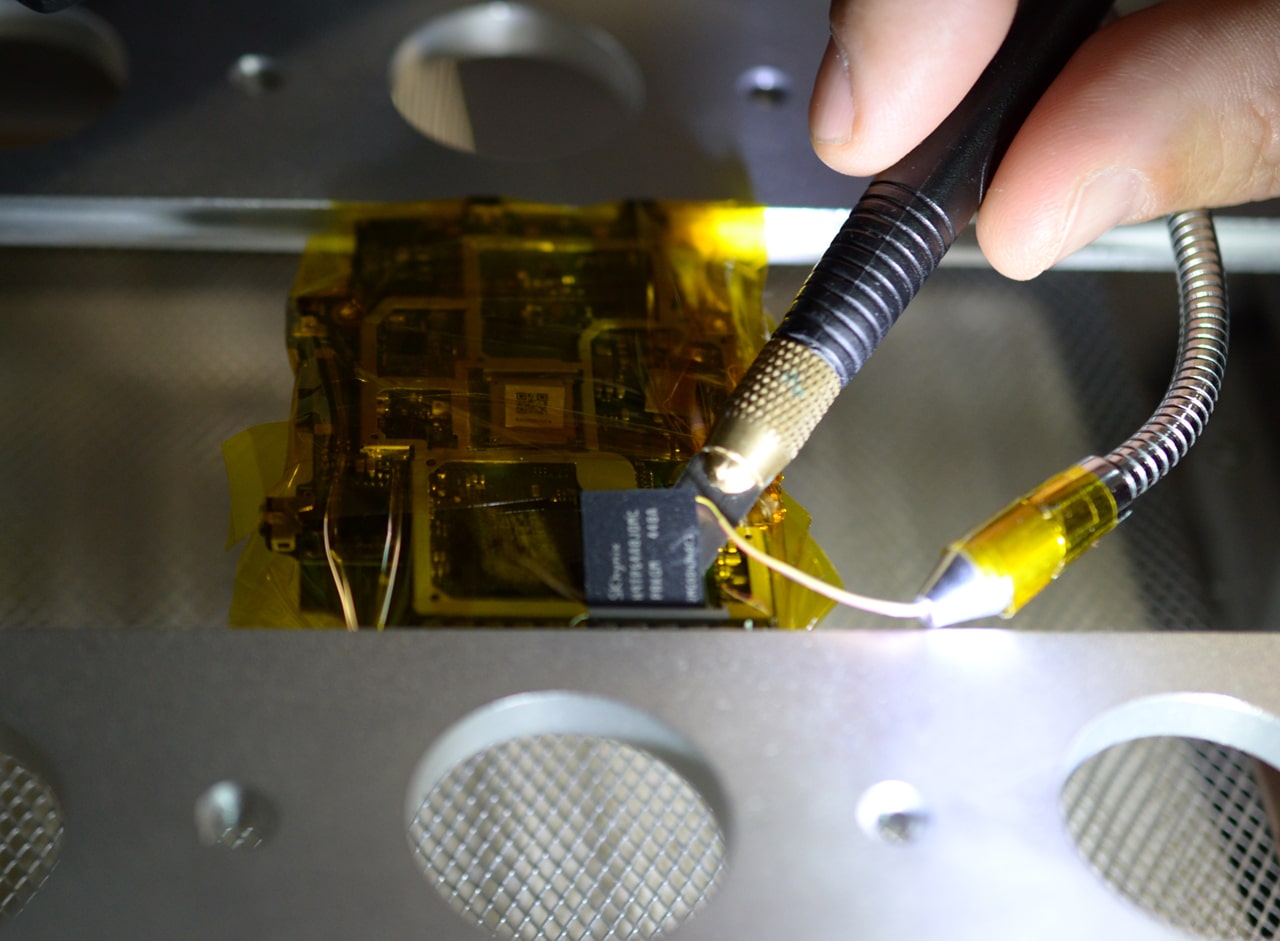
Figure 4. Chip extraction from circuit board
When you unsoldered the chip from the board, you should clean it from compound. The most effective way – to melt it with hot air and remove with solder wick. Make sure your work place is well ventilated – compound evolves aggressive smoke while being heated.
Figure 5. Heating compound with solderer
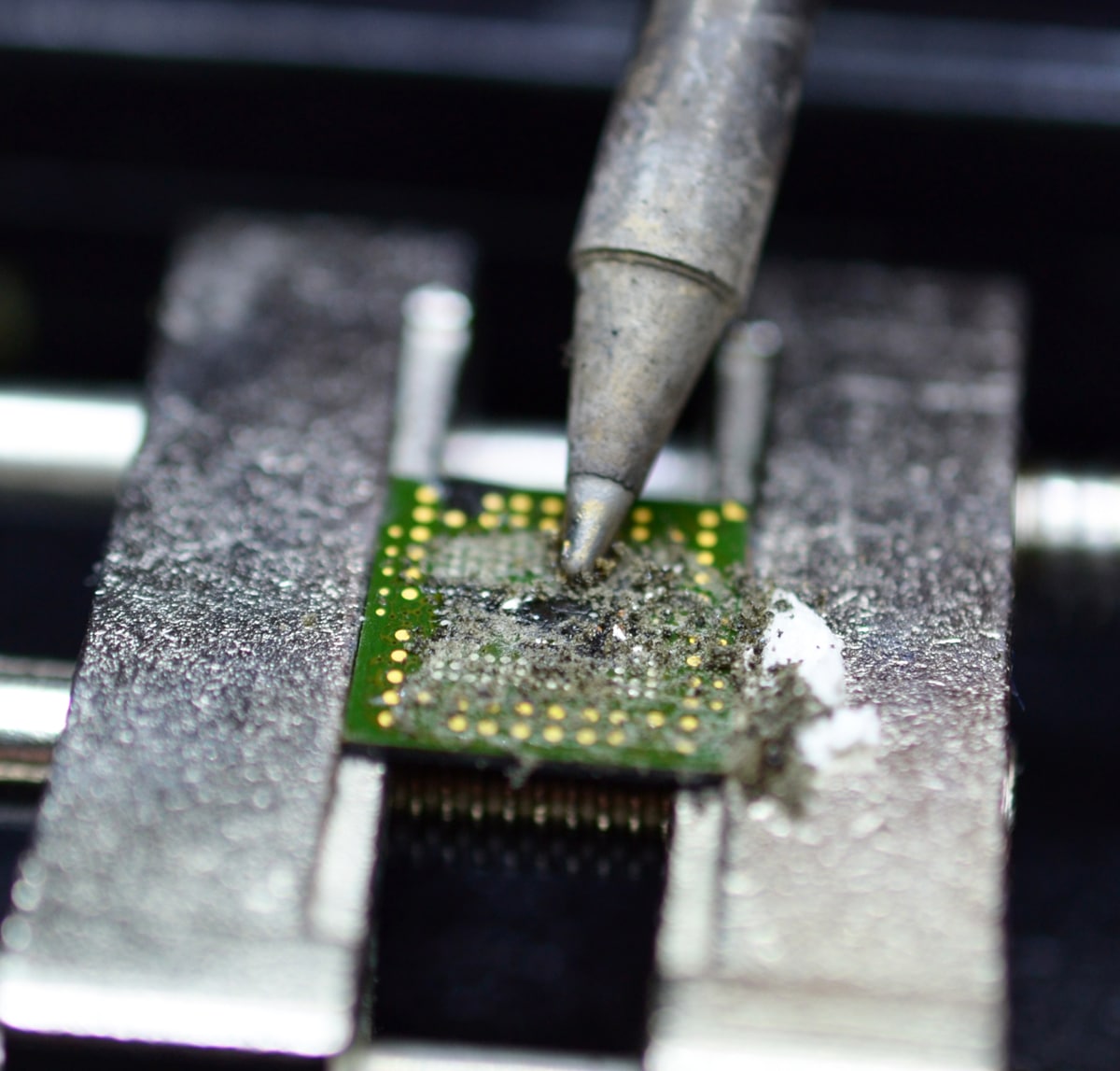

Figure 6. A chip with compound (left), cleaned chip (right)
Practical Chip-off
Here we describe a few cases where chip-off technique was used for data extraction from mobile devices. Such cases are typical for our lab.

Figure 7. An eMMC chip with damaged controller on Rusolut adapter
Case #1. Data extraction from damaged mobile device.
Usually chip-off technique is the only way to extract data from damaged mobile devices. This was HTC M8 smartphone. We extracted BGA chip from it and read the data with PC 3000 Flash. The dump we got was parsed with UFED Physical Analyzer.

Figure 8. Smartphone fragments


Figure 9. eMMC chip

Figure 10. Data extracted from the chip
Case #2. Data extraction from water damaged Nokia Lumia 800 with VISUAL NAND RECONTRUCTOR (Rusolut).
In most cases chip-off technique is the last chance to extract data from water damaged mobile devices. In this case we had water damaged Nokia Lumia 800 (without visible traces, the contact with water was short).

Figure 11. Phone’s circuit board
We unsoldered the chip and put it into special adapter to read the data.

Figure 12. Chip unsoldering

Figure 13. BGA 169 adapter
After we used simple card reader and USB write blocker to read the data.

Figure 14. BGA 169 inserted into card reader
VISUAL NAND RECONTRUCTOR successfully read the dump with rare TexFAT file system.

Figure 15. VISUAL NAND RECONSTRUCTOR – Main Window
Then we carved SMS messages from store.vol.

Figure 16. Carved SMS messages
That’s how we extracted all data needed for investigation. The technique can be used for data extraction from almost all water damaged mobile devices.
Case #3. Data extraction from passcode protected mobile devices (or devices with damaged display)
There are a lot of such cases in our lab. The main problem here – locked bootloaders, so you can’t use the method described in our article Physical acquisition of a locked Android device [12]. Also, top mobile devices don’t allow you to use JTAG technique, so chip-off is the only option.

Figure 17. Passcode locked smartphone

Figure 18. eMMC chip

Figure 19. Data parsed with Oxygen Forensic® Detective
Case #4. Recovering data from mobile devices
That time we examined Microsoft Nokia Lumia 830 (RM-983) running Windows Mobile 8. There is no solution of data recovery from this phone other than chip-off. And again we used an adapter (USB that time) to read the data and recover deleted files.

Figure 20. Microsoft Nokia Lumia 830 (RM-983)

Figure 21. Smartphone disassembly

Figure 22. Phone’s circuit board

Figure 23. eMMC chip
We used a USB adapter to read the data.

Figure 24. USB adapter

Figure 25. Partition structure
Also we use chip-off technique for data recovery from top Android devices. For example, recently we recovered data from HTC One smartphone running Android 6.0. It has locked bootloader, so there is no way to create physical image via ADB. Also we don’t have equipment to extract data from it via JTAG.
Case #5. Data extraction from old mobile devices
Sometimes we need to extract data from very old mobile devices. Usually we can’t even connect such devices to workstation, because they don’t have interfaces. Also, usually there is no way to perform logical extraction either. So the only way to extract data (especially deleted) is using chip-off technique.

Figure 26. JPG header in Sony Ericsson SE-T303 dump
Discussion
Chip-off is the most difficult way of data extraction from mobile devices. This method forces examiner to work with encryption and encoding, unknown or hardly known file systems, new formats of databases. But, nevertheless, nowadays this technique is the most promising, because it can help to extract all the data both from working and damaged mobile devices.
References
- VISUAL NAND RECONSTRUCTOR http://rusolut.com
- VNR Documentation
- RUSOLUT NAND Adapters
- PC 3000 Flash http://www.acelaboratory.com/pc3000flash.php
- eMMC/eMCP 3in1 socket USB,9×11 11×10 11.5×13 12×16 12×18 14×18,eMMC programmer adapter reader, BGA169/153/162/186/221, 3in1 http://aliexpress.com/item/eMMC-eMCP-3in1-socket-SD-9×11-11×10-11-5×13-12×16-12×18-14×18-eMMC-programmer-adapter-reader/32542535705.html
- UFED Physical Analyzer http://www.cellebrite.com/Mobile-Forensics/Applications/ufed-physical-analyzer
- Micro Systemation https://www.msab.com/
- Oxygen Forensics http://www.oxygen-forensic.com/en/
- Belkasoft Evidence Center http://belkasoft.com
- AXIOM https://www.magnetforensics.com/magnet-axiom/
- Android forensic analysis with Autopsy https://www.digitalforensicscorp.com/blog/android-forensic-analysis-with-autopsy/
- Physical acquisition of a locked Android device https://www.digitalforensicscorp.com/blog/physical-acquisition-of-a-locked-android-device/
About the authors:
Interests: Computer, Cell Phone & Chip-Off Forensics
Interests: iOS forensics, Android forensics, Mac OS X forensics, Windows forensics, Linux forensics







Comments are closed.