Creating a digital forensic laboratory is a responsible step. The effectiveness of the laboratory depends on what software, hardware and equipment will be purchased.
DFC specialists took part in the creation and upgrade of several digital forensic laboratories owned by state organizations and private entities and today they will share their tips and tricks.
A FORENSIC WORKSTATION
Choosing a workstation configuration is an important step. The effectiveness of digital examiners depends on the way the workstation is configured.
However, we want to pay special attention to one point: the workstation should work as quietly as possible. Imagine an open space where several powerful computers are installed, each of which makes a noise like a server. The employees’ headache and poor health are guaranteed. Silent workstation performance is achieved by using low-noise fans and passive cooling systems.
Do not use top hardware. The idea to buy the most expensive processor, memory, motherboard for your new workstation is not the best one. We had many problems with the workstation in which similar components were used.
In our opinion, this configuration is optimal today:
OS: Windows 10 Pro 64-bit
CPU (2): E5-2660 v4 (14 core)
RAM: 64 GB DDR-42133 ECC
OS Drive: 1 TB SSD
Temp/Cache/DB Drive: 256 GB SSD
Data Drive: 8 TB 7200rpm
RAID Drives: 5×4 TB 7200rpm
Video Card: GeForce GTX 1080
We recommend to use two or more monitors for each workstation.
The most effective work is achieved when a digital examiner uses two workstations in its work.
Use NET Storages to store cases, forensic images, etc. NET Storages with a volume of 100-150 TB proved to be quite effective.
Use 10Gbit Net Cards. They will allow you to transfer data from the workstation to NET Storages quickly.

A Tableau Write Blockers Kit
FORENSIC SOFTWARE
It’s a good idea to have as more different forensic software in the digital laboratory. This will allow a forensic examiner to make cases as quickly and efficiently as possible. Also, this makes it possible to recheck the results of the research effectively.
However, if you have a limited budget, we recommend buying this software:
Windows 10 Pro
Office 365
Antivirus software
X-ways Forensic
AXIOM (Magnet Forensics)
The rest of the tools can be purchased as the laboratory develops.
Also, a lot of research can be done using freeware tools. Sometimes these tools outperform functionality of commercial tools.

CASE MANAGEMENT SOFTWARE
If you create a digital forensic laboratory in a government organization, for example in the police department, then most likely they have their own case management software and then your task is just to add a new laboratory to the network of existing ones.
In other cases, you can use free and chargeable CRM systems. Besides, some CRM systems can be adapted to your management needs.
We recommend Kirjuri (Kirjuri is a web application for managing cases and physical forensic evidence items.) and Lima Forensic Case Management of all the specialized tools.
VIDEO FORENSICS
We recommend using a separate workstation for the production of video forensics cases. We recommend using the following forensic tools:
DVR Examiner
Amped FIVE
Elecard
Very good results of recovering deleted videos can be obtained using X-ways Forensic. We have written about this tool above.
MOBILE FORENSICS
We recommend using a separate workstation to carry out mobile forensics research.
There are a lot of tools for mobile forensics. That is why it is difficult for a beginner to understand what they need to carry out this research effectively. We recommend using the following mobile forensic tools:
UFED 4PC (with CHINEX, UFED Camera Kit)

Cellebrute UFED Touch

Cellebryte cables and adapters
Oxygen Forensics DETECTIVE
XRY
Elcomsoft Mobile Forensic Bundle
We recommend using SР Flash tool to retrieve data from MTK based phones.
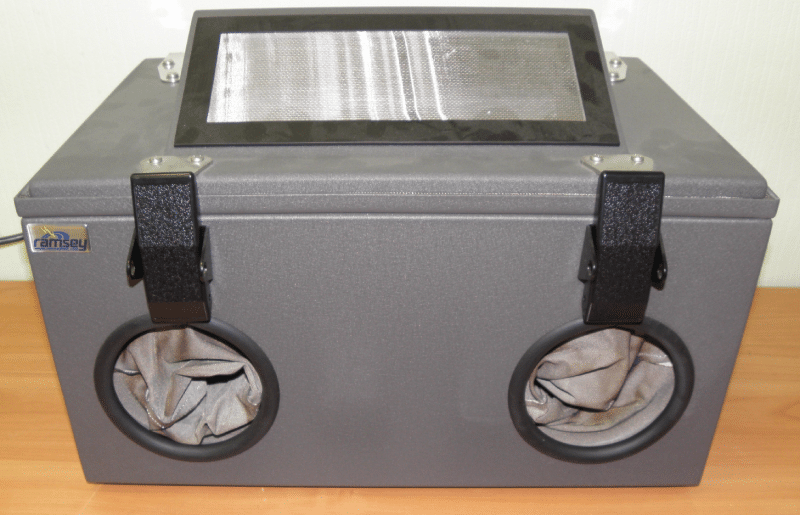
A Faraday Box (Ramsey)
CLOUD FORENSICS
We recommend using the following tools for Cloud forensics:
UFED Cloud Analyzer
Oxygen Forensics DETECTIVE
Elcomsoft Cloud eXplorer
MOBILE DATA RECOVERY
We recommend using flashers for JTAG research:
Easy Z3x JTAG BOX
Octoplus Box
Samsung anyway S101
For Chip-off we recommend using:
VISUAL NAND RECONSTRUCTOR (STARTER KIT, Rusolut)
SMARTPHONE KIT (Rusolut)
CHINESE SMARTPHONE KIT (Rusolut)
NuProg-E UFS/EMMC Programmer
IN-UFS-Socket BGA Opentop
N-UFS-065-BGA095-115130-02O BGA Opentop
N-UFS-050-FBGA153-115130-02O BGA Opentop
We recommend using Weller WHA 300 Hot Air Reworking Station or Ersa HR100 Hybrid Rework system for disordering chips.
DATA RECOVERY (HARD DRIVES, FLASH DRIVES, MEMORY CARDS)
We recommend using a separate workstation for the production of Data recovery. You will need special hardware and tools for data recovery:
PC-3000 Express Professional System (Acelab)
Data Extractor Express (Acelab)
PC-3000 Flash (Acelab)
FURNITURE
Many people believe that it is enough to buy ordinary office desks and chairs to equip a digital forensic lab. However, it is not so. Tables must have abrasion resistant coatings. We recommend the use of special laboratory tables.
Office chairs should be as convenient as possible. We recommend using not ordinary office chairs but gaming chairs.
The table where the electronic equipment is assembled and disassembled should be equipped with an antistatic mat and an antistatic bracelet.
Happy forensicating!
About the authors
Oleg Skulkin, GCFA, MCFE, ACE, is a DFIR enthusional (enthusiast + professional), Windows Forensics Cookbook and Practical Mobile Forensics co-author.
Igor Mikhaylov, MCFE, EnCE, ACE, OSFCE, is a digital forensic examiner with more than 20 years of experience and Mobile Forensics Cookbook author.






Comments are closed.