The function of passwords extraction from dumps of the devices running Windows Phone operating system appeared in the newest version of the program “Oxygen Forensic Detective”. Some users of the program may have question how does it work. In this article, we are going to tell about the function of this program.
Extraction of memory dumps from Windows Phone mobile devices
Windows phone
In order to create a full memory copy of such devices it is recommended to use the following methods:
- Creation of a mobile device memory copy by loading of a special device management program in DFU mode. This method is valid for the devices that were produced before 2014.
- Data extraction from memory chip via debugging interface JTAG (Joint Test Action Group).
- Data extraction from memory chip via In-System Programming method. In-System Programming or ISP – a technology of programming electronic components (PLD, microcontrollers, etc.) that allows to program a component already installed in a device. Prior to this technology, the components were programmed before the installation in a device and in order to be reprogrammed they had to be removed from the device. [1]
- Data extraction from memory chip («Chip-off»).
It should be mentioned that:
- For Windows Phone devices, starting from the series x30, method of data extraction via debugging interface JTAG is not valid as test points were removed from the devices’ system board. At the same time, the method of data extraction from memory chip via In-System Programming became widely used. This method allows to solder conductors directly to the memory chip on the mobile device’s system board and to extract data with much higher speed than when you use the method of data extraction via debugging interface (JTAG).
- Taking into account that a user’s section data encryption or memory chip lock code installation are widely used on the mobile devices running Windows Phone operating system and it is impossible to get an access to the data of the memory chip without knowing the code, the method of data extraction from memory chip («Chip-off») should be used only in case you did not achieve results by other methods.

Figure 1. Log of the locked memory chip analysis.
Password extracting
In order to extract a lock code, you need to open the “Oxygen Software Extractor” program and chose option « Windows Phone 8 JTAG image ».

Figure 2. Main window of the program “Oxygen Software Extractor”.
Locate the full memory copy of a mobile device and press “Next”

Figure 3. Selection of full memory copy of a mobile device.
In the next window, you need to check that the data is put correctly and if it is correct then press “Extract”.

Figure 4. Window of the input data validity check the “Oxygen Software Extractor” program.
After it the process of data extraction from the chosen dump will start.

Figure 5. The process of the dump extraction.
If the file that contains hash code is found in the full memory of the mobile device, the program «Passware Password Recovery Kit Mobile» will start automatically. It will decipher the hash and provide the deciphered data to the program “Oxygen Software Extractor”.

Figure 6. The process of password recovery via «Passware Password Recovery Kit Mobile».
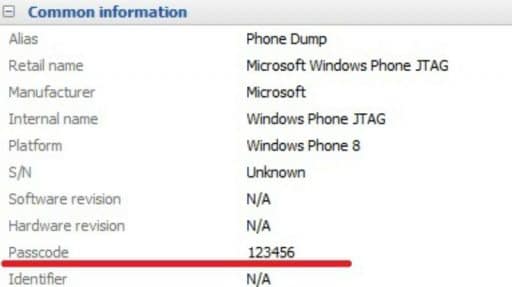
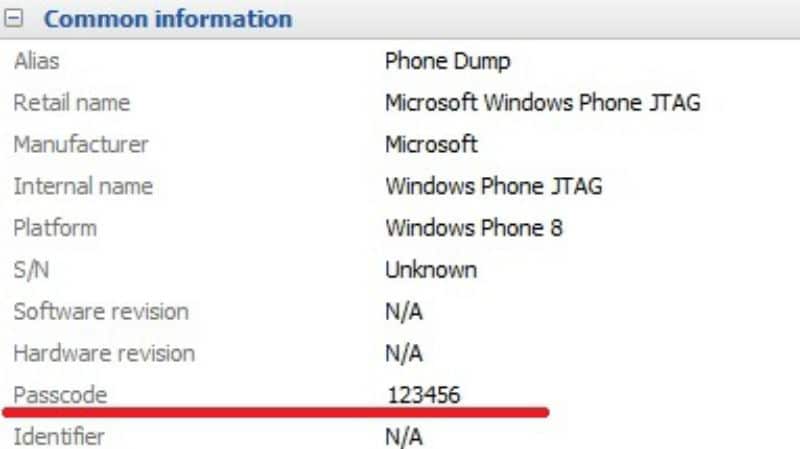
When the data extraction is finished, the screen lock password will be shown in the section “Device information”.

Figure 7. Information about the detected screen lock password.
Conclusion.
An access to the “alive” data that is in the memory of a mobile device can be vital in the specific types of investigations. In this article, we have demonstrated the function of a screen lock password extraction from the full memory copy of the devices running Windows Phone operating system of the program “Oxygen Forensic Detective”.
References:
- In-System Programming – https://en.wikipedia.org/wiki/In-system_programming
Authors: