Examination of JPEG quantization tables has been used in digital image forensics for quite a long time. Using it an examiner can:
- identify imagery processed by software [1, 2];
- identify camera, including its model [1, 2];
- detect double compressed images [3].
Solving of the first two problems is based on the fact that different image editors and firmware of different digital cameras get the same image compression quality using different unique quantization tables. These tables are like signatures, which an editor or camera leaves in a JPEG file.
If you need to identify camera model used for taking of examined picture, you can use EXIF data. But this data can be easily deleted or modified. That’s why quantization tables are more dependable data sources. You can just compare examined image’s quantization tables with quantization tables from a database, for example, FourMatch [4].
But, firstly, such database can’t be full. Secondly, only developers know how such databases are filled. Thirdly, not all forensic examiners has such bases.
That’s why sometimes digital image forensic examiner can’t identify model of camera used for taking the picture. But he can identify if the picture was taken with the camera he got for examination.
When an examiner compares quantization tables, he or she can be surprised.
It’s well known that any digital image editor uses separate quantization matrix for every available quality. All images saved with an editor with same quality have same quantization matrix. One can think that the same works with digital cameras. But the answer is – not always.
Most digital cameras allow to choose one of two or three qualities for picture saving. But some cameras use different quantization matrixes for the same quality. It depends on the fact, was flash used or not. The thing is – there are a lot of light and black parts on images taken with flash. Such parts can be compressed more without visible quality decreasing. So that’s what happens – pictures taken with flash are compressed more than whose taken without it.
But if we analyse pictures taken with different cameras, we learn that flash isn’t the only factor.
For example, OLYMPUS E-M10 uses different quantization matrixes for pictures taken with different ISO. You can see it on the following illustrations:
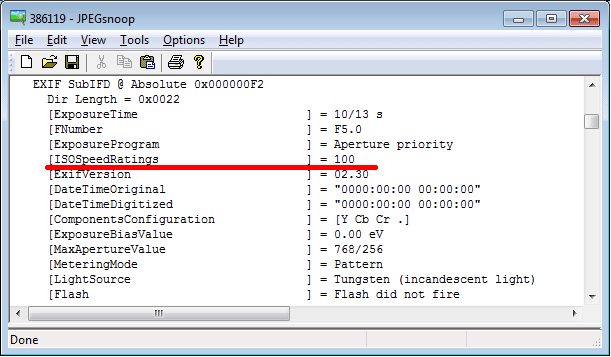
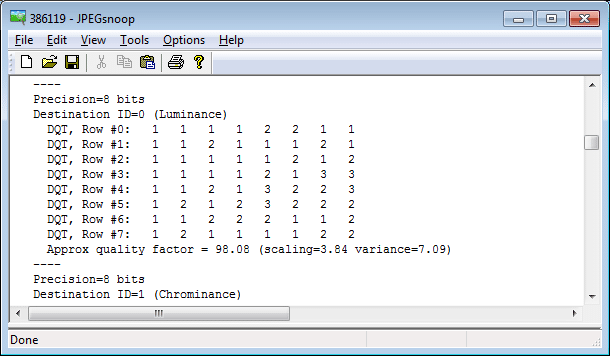
Figure 1, 2. EXIF data (partly) and quantization table of a picture taken with ISO 100
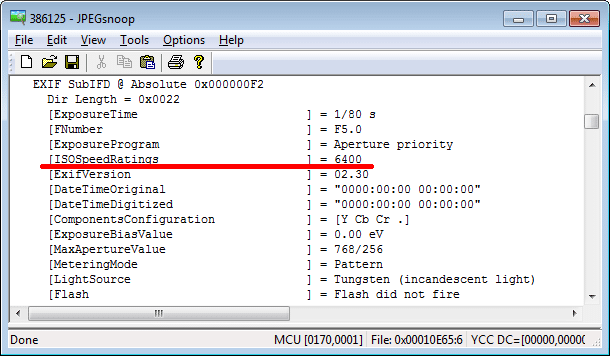
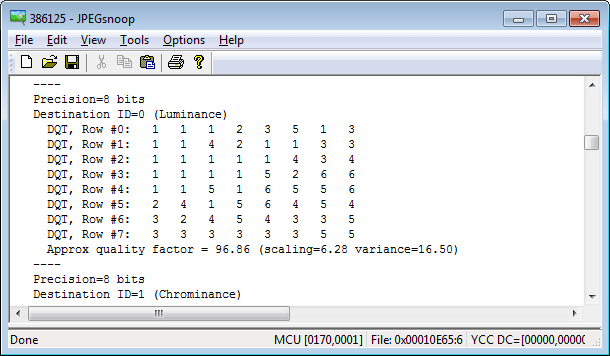
Figure 3, 4. EXIF data (partly) and quantization table of a picture taken with ISO 6400
If an examiner doesn’t know about this, his experiment may fail, because quantization table of questioned picture and quantization table of picture taken with the camera received for examination may not match. This may be because pictures are taken with same camera, but different settings.
References:
- Jesse Kornblum. Using JPEG Quantization Tables to Identify Imagery Processed by Software. https://www.dfrws.org/sites/default/files/session-files/paper-using_jpeg_quantization_tables_to_identify_imagery_processed_by_software.pdf
- Hany Farid. Digital Image Ballistics from JPEG Quantization. http://www.cs.dartmouth.edu/farid/downloads/publications/tr06a.pdf
- Babak Mahdian and Stanislav Saic. Detecting Double Compressed JPEG Images. https://www.google.ru/url?sa=t&rct=j&q=&esrc=s&source=web&cd=2&cad=rja&uact=8&ved=0ahUKEwi5-pSFwsnPAhXpK5oKHTjsBcoQFggmMAE&url=http%3A%2F%2Flibrary.utia.cas.cz%2Fseparaty%2F2011%2FZOI%2Fmahdian-detecting%2520double%2520compressed%2520jpeg%2520images.pdf&usg=AFQjCNGNBOZD-4ZqSubE927psRSy9HVb0w
- FOURMATCH™. http://www.fourandsix.com/fourmatch/
About the authors:
Serge Petrov
Interests: Digital Video Forensics, Forgery Detection, Audio Forensics
Interests: Computer, Cell Phone & Chip-Off Forensics
Interests: iOS forensics, Android forensics, Mac OS X forensics, Windows forensics, Linux forensics







Comments are closed.