This article was inspired by an active discussion in one of the forensic listservs.
A citizen accused of that on his computer found illegal content, but he claims that it was hacked. This article describes how to prove that this is not so, on what forensic artifacts should pay attention to, and how you can use the company’s products Belkasoft.
Scanning the disk image for malware is one thing, yet it rarely proves anything. No malware means nothing, and any malware that does exist does not prove anything. If there IS malware, it does not automatically mean that it indeed downloaded anything. Capturing a memory dump and looking for active VPN sessions may give you a hint of some unusual activities, but again it won’t prove anything. In order to determine whether the hacking will need to watch other factors.
First you must check whether the person was physically present at the scene. Belkasoft Evidence Center (BEC) can gather geolocation from different sources, such as Google Maps apps, browser searches, geo-enabled chats and so on.
Secondly, the construction of a timeline to show the activity occurred. Тhis will help build a relationship between the suspect’s activities and their physical presence at the crime scene.
The third, no less important – is the event logs and registry entries. Event logs and registry entries are a valuable source of information that can prove the presence of the suspect on a particular desktop computer while illegal actions.
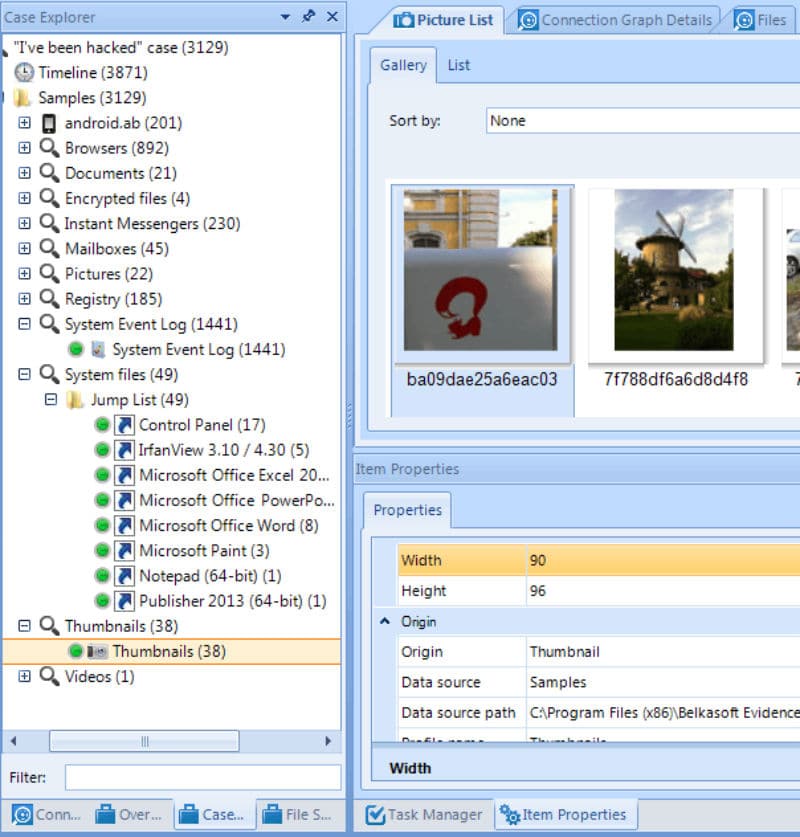
Belkasoft BEC supports searching for thumbnails in any format created by Windows, and if deleted, can carve them.
In the fifth, the thumbnails can not give you an answer that clearly revealed the suspect image, Jumplists can help with this. Jumplists are preserved during Windows updates. And again, if you see someone with completely cleared jumplists, this is at least suspicious.
In conclusion, you can work around the “I’ve been hacked” defense by collecting information from the PC/mobile being analyzed as well as from multiple other sources. Establishing physical presence, proving the use of a certain USB drive and proving access to certain files at certain times can be enough to make a weighted decision.
Here you can not only download Belkasoft Evidence Center, but also to get acquainted with the authors of the article