Information technology enveloped our lives and a smartphone at the moment is not just a means of communication but also data warehouse. For security devices most of the data using encryption, and therefore the complicated access to the data for the investigation.
The law enforcement agencies have invested heavily to obtain and use data from smartphones in investigations and court cases. Cellebrite has become a leading supplier of mobile data capture technology. Cellebrite produces software and mobile terminals, which are used to physically copy data from cellular phones seized data that can not be distributed via a connection which can be intercepted.
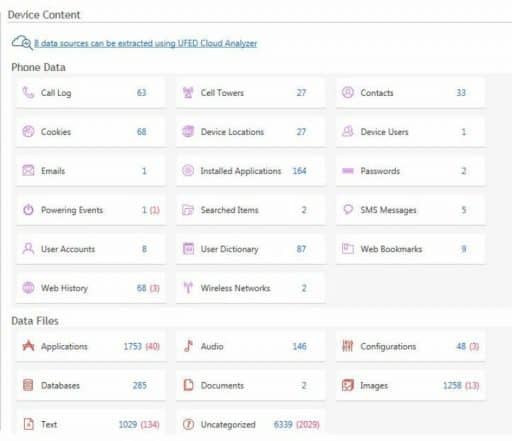
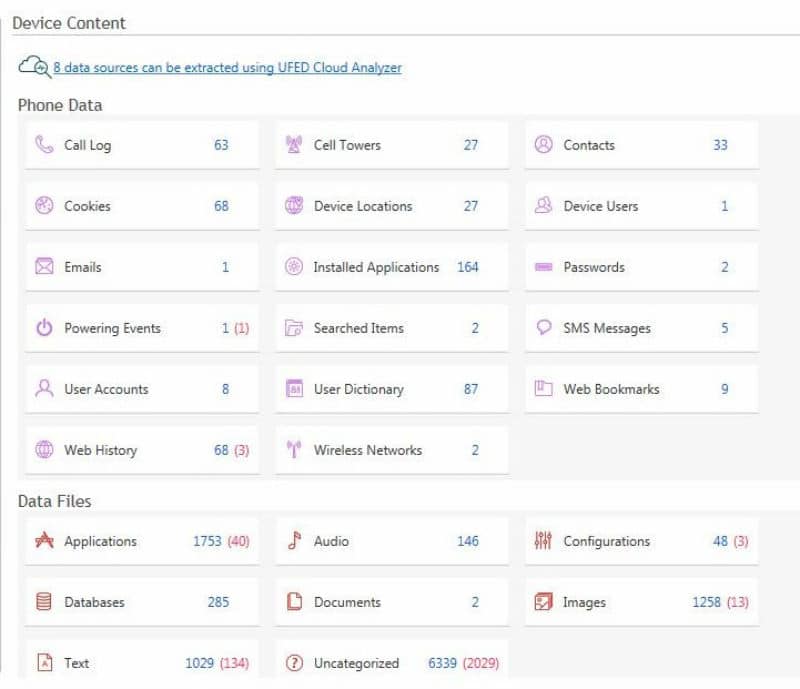
Cellebrite UFED line offers (Universal Forensic Extraction Device) hardware and software to governments for them to copy as much data as possible from the seized smartphones. UFED directory contains procedures for retrieving data from more than 95 percent of mobile devices on the market. These procedures can be as simple as accessing the built-in backup and debug functions in a smartphone with weak security. The company claims that it can download virtually every piece of data from virtually any device, on behalf of the police intelligence services in more than one hundred countries. It does this by taking the phone seized from the police, and then plugging it in, and retrieving messages, phone calls, voice messages, pictures, and more from the device using its own patented technology. It then generates a report extraction that allows researchers to see at a glance where a man was with whom they talked, and when.