Sextortion emails have become an increasingly common form of cybercrime, preying on fear and shame to extract money from victims. These emails typically claim to have compromising material, such as intimate photos or videos, and threaten to expose the content unless the victim complies with the criminal’s demands.
While many of these threats are fake, others may stem from genuine breaches of privacy. To better protect yourself, it is essential to understand the two main types of sextortion emails: legitimate threats and malware scams.
Real Sextortion Threats or Hacking Attempts.
Legitimate sextortion threats occur when a cybercriminal is able to catfish a victim and obtain compromising material. This content is typically shared with the victim’s consent but later used as leverage to extort them with the threat of leaking it to friends, family, or professional networks, a crime formally known as Non-Consensual Intimate Image Sharing (NCIIS).
Malware email scams, also known as “you’ve been hacked” email sextortion, are attempts to breach personal data. These emails typically make vague claims and pressure victims to click on links or download attachments, which can infect their devices with malware. These scams use the fear of sextortion and exposure to trick victims into giving access into their systems.
By distinguishing between these two types of threats, individuals can respond more effectively and avoid falling victim to either.
Understanding the Two Types of Sextortion Emails
In a case of sextortion, the blackmailer may communicate their threats or expose the victim using email, but the threat likely did not originate from a breach of your computer’s security or a hacking of your webcam. If you’ve shared intimate content through social media or dating applications, you are naturally at risk.
Emails associated with real sextortion threats differ from those used in malware scams. Below are common features of a true sextortion email threat:
- The blackmailer includes proof of their evidence. In cases of online blackmail, the culprit often displays their leverage to elicit compliance from their victims, typically by including one or more screenshots of the compromising content in the email.
- They provide details on how they will expose you. Real sextortionists often use catfishing tactics to learn personal details about their victims. They may threaten to share the compromising content with specific friends, family members, or colleagues.
- They demand non-recoverable payment methods. Common payment methods include gift cards, prepaid debit cards, or other forms of payment that are difficult to trace and cannot be reversed or disputed.
Malware scams attempt to mimic the structure of real sextortion emails, but their goals and tactics reveal their true nature. These scams aim to extort victims by tricking them into installing malicious software. Key indicators of a malware scam include:
- Claims of hacking your device or webcam. The email may include an arbitrary date when the scammer claims to have hacked your system to make the threat seem more credible. This type of webcam blackmail will normally include a claim that the hacker has access your contact list and will send the content to those contacts.
- A random photo to bolster the threat. Scammers often include an unrelated image, such as a Google Street View photo of your home or a previous address. In some cases investigated by Digital Forensics Corp., the photos were of locations the victims had lived at years prior.
- Links in the email. These may be payment links or links to the alleged “evidence” the scammer claims to have. Clicking these links is the scammer’s ultimate goal, as they may lead to malware installation.
Side-by-Side Comparison of Threats
To better understand the differences between legitimate sextortion threats and malware scams, consider the following comparison:
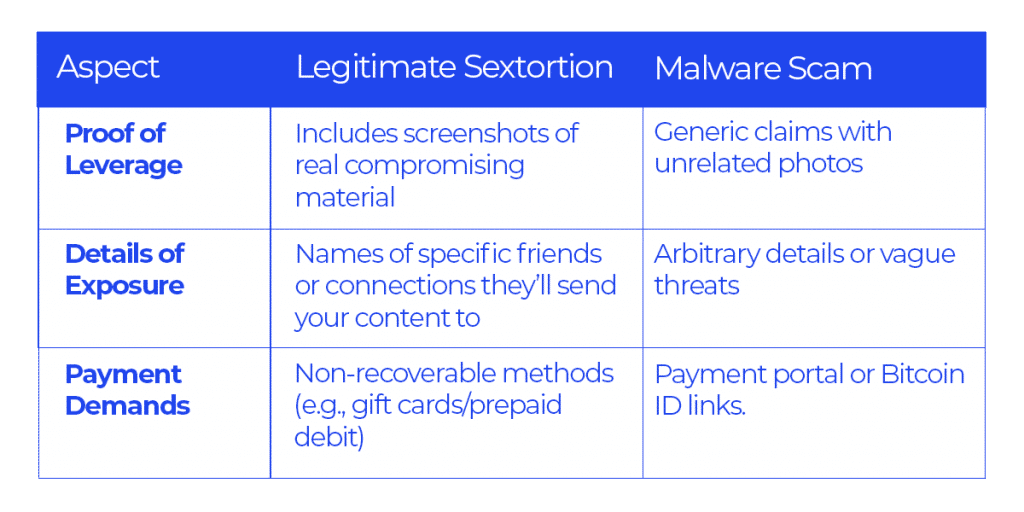
By understanding these distinctions, you can better evaluate the credibility of a sextortion email and respond appropriately. Remember, scammers thrive on fear and uncertainty, so staying informed is your best defense.
When to Be Concerned.
If, after reading the information above, you determine the nature of your threat, consider the following steps for each scenario:
How To Deal With A Real Sextortion Email.
If after reading through the chart you believe you are facing a real sextortion threat, do not panic or comply with the scammer’s demands. Instead, document the threat by taking screenshots and saving any related correspondence before proceeding with the following steps:
- Delay the blackmailer. The ultimate goal of any sextortion scam is to pressure you into paying. Instead of reacting immediately, use strategic delay tactics to slow down communication. This buys you valuable time to seek help from the right professionals.
- Report the incident to the proper authorities. This may require you to file a report with both your local police as well as the national organization designated for cybercrime in your country. In the U.S., the FBI’s Internet Crime Complaint Center (IC3) is the primary organization to contact for sextortion cases.
- Consult cybersecurity professionals. While law enforcement focuses on prosecuting sextortion crimes, private companies can help prevent exposure. Experts in digital forensics can identify the origin of the threat and work to remove the blackmailer’s leverage.

Steps To Take if Targeted by a Malware Scam.
DO NOT CLICK ON ANY LINKS OR ATTACHMENTS. While you should report the incident to authorities, your first priority should be securing your devices and identity. If you are targeted by this scam, it may indicate that some of your data is already in use by scammers.
- Run a malware scan. If you have updated antivirus software, perform a comprehensive scan to detect and remove potential threats.
- Report the email as phishing. Notify your email provider by marking the email as phishing and consider updating your passwords to secure your accounts.
- Seek professional assistance. If you are unsure how to scan your devices, contact a cybersecurity provider. They can perform diagnostic scans, analyze the email’s header, and determine if your data has been compromised.
- Report to law enforcement. Once directed to do so, delete the email and block the sender’s address.
Proactive Cybersecurity Practices
In both cases, maintaining a proactive approach to cybersecurity is essential. Regularly updating your software, using strong passwords, and enabling two-factor authentication can help protect your accounts and devices from potential breaches. By taking these steps, you can reduce your vulnerability to sextortion emails and other cyber threats.
Do You Need Help? Contact Digital Forensics Today.
As a cybersecurity firm specializing in incident response, Digital Forensics Corp. offers services for sextortion email cases. Reach out to our trusted professionals at the Sextortion Helpline for immediate assistance navigating the situation and preventing further harm. With vigilance and education, you can overcome the fear and uncertainty scammers seek to exploit and safeguard your digital life.
DISCLAIMER: THIS POST IS FOR INFORMATIONAL PURPOSES ONLY AND IS NOT TO BE CONSIDERED LEGAL ADVICE ON ANY SUBJECT MATTER. DIGITAL FORENSICS CORP. IS NOT A LAWFIRM AND DOES NOT PROVIDE LEGAL ADVICE OR SERVICES. By viewing posts, the reader understands there is no attorney-client relationship, the post should not be used as a substitute for legal advice from a licensed professional attorney, and readers are urged to consult their own legal counsel on any specific legal questions concerning a specific situation.







