Sextortion is a growing issue all across the world, targeting both minors and adults. The FBI has seen a massive increase in reported cases in recent years. There was a 20% jump in cases in a six-month period in 2023 versus the previous year(1), which itself had seen ten-times the reports of 2021(2).
These figures are continuing a steep rise that requires wide-spread discussion of the dangers of online sextortion. But many people are still unaware of what the term means. We would like to champion the conversation advising those most vulnerable of the perils of sextortion and the best ways to prevent yourself from becoming a sextortion victim.
What is Sextortion?
To properly combat sextortion, it is required to understand what it is and how it differs from other crimes that are often mistaken for it. Keep reading for an overview on sextortion.
Definition and Overview of Sextortion
Sextortion, short for sexual extortion, is the practice of coercing intimate images from a victim which can then be used to blackmail the individual into sending money or more explicit material.
It differs from traditional extortion and other forms of online blackmail due to the material which is being used as leverage. The perpetrator will typically employ social engineering tactics to gain the victim’s trust.
They will use this trust to persuade the victim into sharing explicit photos, often through emotional manipulation or sharing manufactured explicit content first. Once they receive this sensitive content, they blackmail the individual with threats of leaking the content. The threat is usually to do so through direct messages to the victim’s friends, family members, or coworkers.
Types of Sextortion
The different forms of sexual extortion are determined based on the motive of the blackmailer. Learn about the differences of each form of sextortion listed below.
- Financial Sextortion: This involves the perpetrator demanding financial compensation in exchange for not leaking the intimate photos of the victim. This is the true definition of sextortion and the most prevalent form, with roughly 79% or perpetrators seeking money(3).
- Image-Based Abuse: This is an umbrella term that encompasses sextortion. This includes any harmful use or distribution of sexual material, both legitimate and digitally altered, in order to force a victim to do something against their will.
- Sexual Coercion/Sexploitation: Like financial sextortion, this form involves the perpetrator using explicit photos as blackmail leverage. However, it differs in the desired outcome, which is to coerce the victim into providing further sexual material or favors. This is why this crime is more often referred to as sexploitation instead of sextortion.
Legal Landscape of Sextortion in the U.S.
There are laws at both the federal and state level that are in place to prevent and punish criminals that extort through the use of sextortion. However, the way in which each institution defines sextortion create varying protections and ability to prosecute criminals.
Legal Definitions of Sextortion
The FBI defines sextortion as a crime in which someone threatens to distribute private and sensitive material if the victim does not provide them with images of a sexual nature, sexual favors, or money in the case of financial sextortion.
Any form of interstate commerce used for the purposes of extortion of any kind are illegal under federal law 18 U.S.C. § 875. You can read more about federal laws that protect against sextortion here.
While sextortion and all of its forms are clearly defined at the federal level, things begin to get a little more complex at the state level. Some states have clear laws prohibiting sextortion while others interchangeably use the terms sextortion, sexploitation, blackmail and revenge porn. These are all different crimes that require clarity, and the lack of differentiation can cause confusion.

States with Clear Sextortion Laws
California: Under California’s extortion law, Penal Code § 518(4), sextortion is a form of blackmail. It pertains to cases in which the perpetrator’s demands involve sexual conduct or an image of an intimate body part.
Committed sextortion is considered a “straight” felony offense, meaning it can only be charged as a felony holding a punishment of two to four years in prison and/or a fine of up to $10,000.
Attempted sextortion is a “wobbler” offense, meaning it can be considered either a felony, which carries 16 months to three years in prison and/ or a fine of up to $10,000, or a misdemeanor carrying up to one year in prison(5).
Texas: Under Texas’ sexual coercion law, Penal Code § 21.18(6), sexual coercion is a state jail felony offense. It pertains to the threats of illegal action if the victim does not provide intimate visual material, sexual favors, or monetary benefit.
The penalty for such a crime is a prison sentence ranging from 180 days to two years and/or a fine of up to $10,000. For repeat offenders, the crime is increased to a third-degree felony which increases the sentence to between two and 10 years(7).
Texas law also prohibits the recording, digital production, disclosure, and electronic transmission of sexual material without the consent of the individual depicted under Penal Code Chapter 21(8).
New York: New York Penal Law § 135.60 considers the act of inducing a person to do something against their will, including sharing sexually explicit content, with threats against their wellbeing to be coercion in the third degree, which is a class A misdemeanor(9).
Under Section 135.61, the crime is considered coercion in the second degree if the person is coerced into vaginal, oral, or anal sexual contact. This is considered a class E felony(10).
The penalty for a class A misdemeanor in New York can include up to one year in prison, up to three years of probation, and/or a fine of up to $1,000(11). Class E felony convictions can carry a sentence of one to four years, up to five years of probation, and a fine of up to $5,000 or double the gain from the crime(12).
Florida: Florida Statute 836.05 criminalizes the use of threats to cause physical or reputational harm to an individual as a means to extort money or coerce the victim to take actions against their will(13).
The crime is considered a felony in the second degree, which carries penalties including a prison sentence of up to 15 years and a fine of up to $10,000(14).
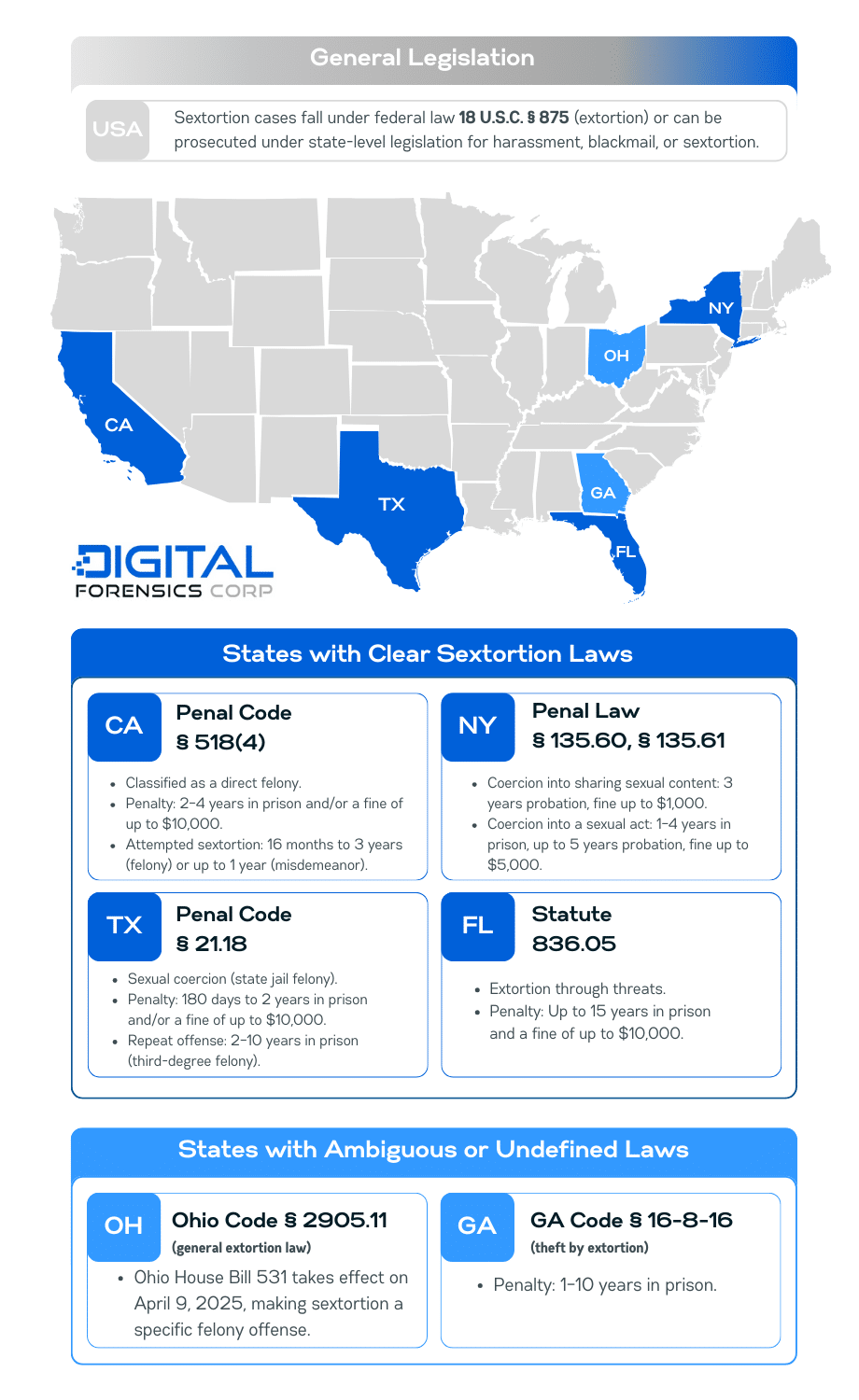
States with Ambiguous or Undefined Laws
In some states, sextortion is not explicitly defined, leading to the use of broader laws, such as blackmail or cyber harassment. Examples of such states will be reviewed, including:
Georgia: While Georgia Code § 16-11-92 is titled Sexual Extortion, the language in the law actually lists sexploitation(15) With the law prosecuting those that coerce for sexual favors You can learn more about the difference between the two crimes by reading our article on Sextortion vs Sexploitation.
Sextortion, in it’s true meaning, is addressed under GA Code § 16-8-16, which covers theft by extortion. The crime carries a punishment of one to 10 years in prison(16).
Ohio: Currently, Ohio state law only prohibits extortion under Ohio Code § 2905.11(17), which includes the use of threats to expose information that would harm an individual’s reputation to obtain any valuable benefit.
However, Ohio will soon join the states in the previous section. Gov. Mike DeWine enacted Ohio House Bill 531on January 9, which criminalizes Sextortion specifically as a felony. The law will go into effect on April 9. Greater detail on Ohio’s new sextortion law can be found here.
The Need for Federal Legislation on Sextortion
With the variance in laws at the state level, there is a growing need for uniform federal regulation on sextortion. Other states use different legal principles, which we outline in our full article “Sextortion Laws Across the US”. These inconsistencies and gaps can harm victims’ ability to seek justice.
“Sextortion occurs at the intersection between corruption and sexual exploitation and for that reason that it tends to fall through the cracks and not get addressed by either,” said Senior Advisor of the International Association of Women Judges Nancy Hendry(18).
Legislative reforms are necessary not only in the US, but on the world stage. The FBI and its international partners issued a joint warning on the growing global sextortion crisis in 2023(19).
Some countries are taking action, but an update of the UN’s vague stance on corruption could help stop sextortion. However, this needs to coincide with an increase in global awareness(18).

Common Tactics Used in Sextortion
Each incident of sextortion is carried out through different methods. Understanding the techniques used by these criminals is pivotal in avoiding these scenarios.
Grooming Victims Online
Sextortionists are crafty and often do their research on a victim to understand what appeals to them. They will use this knowledge to start conversations that seem innocuous and establish trust with their target.
Once this relationship is built, they will continue to collect data on the target under the guise of having shared interests. Then, they use this data to coerce the individual into sending intimate material.
Creating Fake Online Identities
These cybercriminals usually hide behind fake identities to remain anonymous and deceive their victims. They will often pose as a potential romantic partner, professional connection, or even a known friend of the victim.
Through the use of these façades, the perpetrators can trick victims into believing they are a trusted entity. This enables them to extract private information they can use as leverage.
Threats of Exposure and Shaming
Once they receive the intimate photos, the online sextortion begins. Perpetrators feed into their target’s embarrassment by threatening to post the material online or send it to the victim’s family or work contacts.
Sextortionists apply pressure by illustrating the damage that will be done to the sextortion victim’s personal and professional image if this material leaked. They play on an individual’s shame to compel them to meet their requests.
Financial Demands
Once the sextorter has leverage , they will begin making demands. They often claim that they will delete the content if the victim sends them a certain amount of money.
These requests are likely to only intensify if the victim caves. With complete control of the situation and an already-displayed lack of honesty, the perpetrator has no incentive to actually delete the content knowing that the victim is willing to pay creating a cycle of constant extortion until the sextortion victim either is ruined financially or takes the steps to stop the blackmail.
Psychological Manipulation and Control
The beginning of the scam will often involve the blackmailer using a catfish account to message and manipulate the victim through deceptive techniques of flattery, seduction, and love bombing. However, this takes a dark turn when the perpetrator gains leverage in the form of the victims sexual content.
Once they’ve received the intimate photos, the bait and switch commences. They often use threats and language that is meant to isolate the victim and make them feel like there’s nowhere to turn. They elevate the victim’s fears and guilt-trip them by casting blame and making them feel prurient for sending the content.
Typical Sextortion Cases
There are many different ways in which an incident of sextortion can be carried out. Each of these methods hold varying potential to cause harm to the victim.
Case 1: Romance Scam-Based Sextortion
These cases typically move quickly and can take place on both dating sites and social media platforms. The perpetrator poses as a fake romantic suitor to gain the victim’s trust and initiate sexual conversation using a tactic known as catfishing.
They then take advantage of this situation by coercing the victim to exchange explicit photos with someone they believe is a romantic partner. With this content, they blackmail the victim with threats of leaking the sexual media if they don’t comply.
Case 3: Deepfake Sextortion
In some sextortion cases, the perpetrator doesn’t gain access to intimate photos of the victim. Rather, they find high-quality images of the individual online and impose them over existing explicit content.
This deepfake media has been used more often in social media sextortion cases recently. To learn more about how this is done and steps you can take to prevent it, read our articles on deepfake sextortion and oversharing online.
Case 4: CamGirl Sextortion
Platforms that allow models to livestream adult content have become a tool for online sextortionists. The ability to interact and make requests to these models adds a level of believability that prerecorded content cannot.
The models may be complicit in the crime, forced to create content, or even be unaware that their content is being stolen and used.
Case 5: Sextortion Emails.
These types of attacks go by many names, such as phishing, malware, and “You’ve been hacked” sextortion emails. While these each use slightly different techniques, they all revolve around the perpetrator claiming or providing evidence that they’ve gained access to your intimate content.
They will then either request that you pay them or tell you to click a link which contains malware that will actually provide them access to the content they claim to have.
A Real Case of Sextortion and Survival: The Case of Nathan McErlean
Nathan McEarlen, at the time a 25-year-old postman from Northern Ireland, was visiting Santa Ponsa when he was added on snapchat by an unknown woman. Their convincing conversation went on for weeks before things turned sexual.
Upon receiving an explicit photo, McEarlen completed the “other half of the dance(19)” and was immediately met with screenshots of his explicit content and threats of leaking it if he didn’t send £3,000.
McEarlen refused to pay, claiming that he didn’t care if the sextorer followed through on their threats. The perpetrator did just that, adding contacts they obtained through his digital footprint to an Instagram group and sharing the photo.
After realizing what happened, McEarlen made his account private, reported the incident to Instagram, and warned his following of the situation. While McEarlon took the leak well, this is not always the case and displays the risks of not seeking assistance.
What to Do if You Are a Victim of Sextortion
Falling into a sextortion scam may make you feel helpless, but there are steps you can take to gain control of the situation. Remember you are not alone and there is help, but you need to act fast.
Immediate Steps to Take
The first thing you should know if you become a victim of sextortion, is that you should never pay or comply with the blackmailer. Meeting their demands will not make them go away, it will only turn you into their cash cow.
In an effort to give yourself some time and avoid a potential content leak, we suggest using delay tactics to avoid paying the blackmailer and then cutting of communication.
Cutting off communication is advisable, but you should not block the perpetrator. Not only could this incite a retaliatory leak of your content, but it may also inhibit law enforcement and cybersecurity professionals from properly assisting you.
You need to begin collecting evidence of the crime. The accounts used by the perpetrator and chat logs containing threatening messages are critical when filing a police report.
Reporting Sextortion to Authorities
You should start by filing a police report with your local law enforcement. They can help you resolve the case or point you in the direction of the proper national agency in your region.
- US – Incidents of sextortion are handled by the FBI. Minors should report sextortion to NCMEC.
- Canada – Report sextortion to the Canadian Anti-Fraud Centre. Minors can file reports through Cybertip.
- UK – The National Crime Agency provides resources to sextortion victims. Adults can file a report to the Metropolitan Police Service and minors can file reports through CEOP.
- AU – Australia’s eSafety Commissioner supplies tips for dealing with sextortion.
Reporting Sextortion to Online Platforms
Most social media platforms have ways to report sextortion to their site administrators. This can help have your attacker’s account removed and take your media down from the platform. You can learn more through our articles on reporting blackmail on social media below.
Leveraging Cybersecurity Professionals
Cybersecurity agencies can help you take control of the situation. Their expertise enables them to track down the identity and location of cyber criminals through techniques such as IP tracing and taking steps to remove the leverage and prevent content leaks.
Additionally, the aid of cybersecurity can help prevent you from falling victim to similar attacks in the future. They can help discover security risks in your online presence and advise you with precautions to take moving forward.
Legal and Psychological Support
After collecting the evidence to build your case, you should seek the advice of a legal consultant. They can help you understand your rights and take the appropriate legal action.
Many of the national agencies previously discussed also provide information on resources for psychological support that can help you deal with the trauma of sextortion.
Prevention Strategies for Sextortion
Understanding how sextortion scams operate is the first step in protecting yourself. Many victims fall prey to these schemes because of common sextortion misconceptions, such as believing that scammers always have real compromising material or that paying will make the problem go away. In reality, scammers often rely on fear and manipulation rather than actual evidence.
To stay safe, follow some of the steps outlined in the sections below.
Privacy Settings on Social Media
Each platform has settings that can help limit sextortionists from accessing your profile. Making your account private can help limit their ability to reach you, gain information to manipulate you, take away access to your photos, and prevent them from contacting your followers.
Below are some helpful resources for securing your social media accounts:
Avoiding Sharing Intimate Content Online
Sharing intimate content is a risky practice even when it’s sent to people we know. This is only amplified if the recipient is somebody whose identity is unconfirmable. Photos sent in private or temporary conversations can easily be downloaded and made public.
Early Identification of Sextortion Red Flags
If you believe you’ve been contacted by a scammer, it’s important to know the warning signs. Someone who is requesting intimate images, personal information, or money and wants to keep things secret likely isn’t who they claim. If you feel like something’s off, it probably is.
Role of Technology in Sextortion Prevention
While technology can be used to commit cybercrimes, it can also be used to combat them. Understanding how to utilize the tools at your disposal can increase your chances of successfully stopping sextortion.
Digital Forensics in Investigating Sextortion
Digital forensics experts can help you track down your blackmailer and remove your content from their grasp. Their ability to locate the perpetrator and monitor their online presence can provide you with evidence that is necessary for seeking justice.
Once this evidence is in hand, digital forensics experts can connect you with the proper law enforcement agencies with jurisdiction to properly prosecute these criminals, regardless of their location.
Technology for Monitoring Online Activity
There are tools and software designed to monitor online activity, especially for children and vulnerable individuals, to help prevent sextortion from occurring in the first place.
Services such as Take It Down can help prevent the spread of intimate media while keeping the victim anonymous.
You Don’t Have to Be a Victim.
Online sextortion is a rapidly growing problem that requires universal action to combat. While there is a need for stronger regulations that specifically prohibit this type of crime, there’s an even higher demand for better understanding of its complex nature and risks.
The best way to protect potential victims from being sextorted is to educate them on ways to prevent it. Spreading awareness of the resources available that provide sextortion tips can help those most susceptible avoid these circumstances.
If you believe that you or someone you know has experienced any of the maneuvers covered in this article, reach out to our Sextortion Helpline today.
Sources:
- Sextortion: A Growing Threat Preying Upon Our Nation’s Teens — FBI
- FBI Warns of “Horrific Increases” In Sextortion Schemes That Have Already Victimized Thousands of Children Online – The Debrief
- Sextortion: It’s more common than you think | ICE
- California Code, PEN 518.
- What is “sextortion” under California law?
- Texas Penal Code Section 21.18 – Sexual Coercion
- PENAL CODE CHAPTER 12. PUNISHMENTS
- PENAL CODE CHAPTER 21. SEXUAL OFFENSES
- New York Penal Law Section 135.60 – Coercion in the third degree
- New York Penal Law Section 135.61 – Coercion in the second degree
- New York Class A Misdemeanor Laws and Penalties Guide – LegalClarity
- New York Class E Felony: Sentencing and Penalties Guide – LegalClarity
- Chapter 836 Section 05 – 2011 Florida Statutes – The Florida Senate
- Florida Felony Classifications and Penalties Explained – LegalClarity
- Georgia Code § 16-11-92 (2022) – Sexual Extortion :: 2022 Georgia Code :: U.S. Codes and Statutes :: U.S. Law :: Justia
- Georgia Code § 16-8-16 (2023) – Theft by extortion :: 2023 Georgia Code :: U.S. Codes and Statutes :: U.S. Law :: Justia
- Section 2905.11 – Ohio Revised Code | Ohio Laws
- Pressure builds worldwide for legal protection against sextortion | International Bar Association
- International Law Enforcement Agencies Issue Joint Warning about Global Financial Sextortion Crisis — FBI
- Sextortion on Snapchat is not the end of my world, says victim
DISCLAIMER: THIS POST IS FOR INFORMATIONAL PURPOSES ONLY AND IS NOT TO BE CONSIDERED LEGAL ADVICE ON ANY SUBJECT MATTER. DIGITAL FORENSICS CORP. IS NOT A LAWFIRM AND DOES NOT PROVIDE LEGAL ADVICE OR SERVICES. By viewing posts, the reader understands there is no attorney-client relationship, the post should not be used as a substitute for legal advice from a licensed professional attorney, and readers are urged to consult their own legal counsel on any specific legal questions concerning a specific situation.
The information presented in this article is based on sources that are not readily available to the public and may be subject to restrictions or confidentiality. It is intended for informational purposes only.







