Nowadays, the basic exchange of information is carried out through Instant Messengers by using social networks. Some social networks have their own mobile apps which functionality can be compared with that of IM Messengers.
Where is History of Instant Messengers stored?
Some Instant Messengers store history locally (on a computer or mobile device) such as Skype, WhatsApp, etc.
Some Instant Messengers store history partly locally, partly in the cloud such as Telegram, etc. The amount of information stored locally can be different. For example, it can be account info, cache, chats, calls or maybe just account info, cache.
Where can I find the history of Instant Messengers?
1) Physical dumps of mobile devices.
2) File systems of mobile devices.
3) Backups (history of Instant Messengers can be present in backups completely or partially, depending on the security settings of the operating system of the mobile device). Backups can be detected on computers (or laptops), clouds: Google Cloud, iCloud, etc. Backups can be “standard” (made by using ADB for Android devices, iTunes for Apple devices), and “non-standard”, for example Smart Switch backup (backup made by the proprietary Smart Switch utility (Samsung), or a backup made by the program DrFone (Wondershare) Practice shows that owners of mobile devices do not always realize that when a mobile device is connected to a computer, backup can be created automatically. Therefore, the owner of the device may not take measures to destroy such backups.
4) Hard drives.
5) Memory cards.
6) RAM memory dumps.
7) For Instant Messengers such as Telegram, data can be extracted from their Clouds.
Belkasoft Features
Belkasoft can analyze and extract History of Instant Messengers from mobile devices, PCs, laptops, clouds.

Supported Operating Systems:
- Android
- iOS
- MacOS
- Linux
- Windows
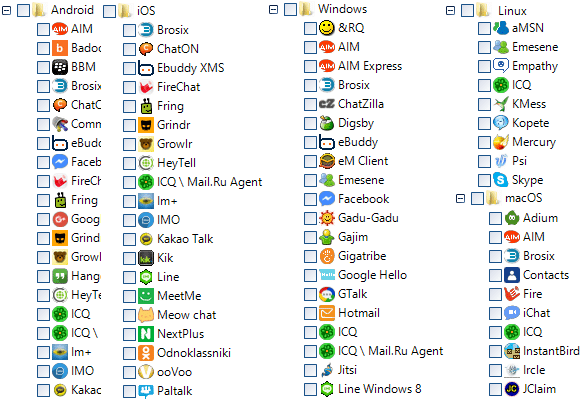
* This list is not exhaustive
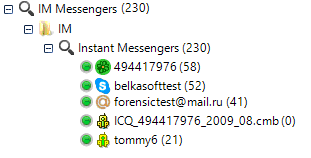
BEC (Belkasoft Evidence Center) automatically locates and extracts chat history from hundreds of Instant Messengers
Instant Messengers usually store its history in a SQlite file. Therefore, if it is not possible to extract its chats for a Instant Messenger, it can be done manually using SQLite Viewer, integrated into Belkasoft.

An example of a restored chat from SQLite-file
Example of the Instant Messenger analysis: Skype
The main data of the work of this messenger is in the file main.db
Main.db location:
Windows 7 or higher: ROOT\Users\%userprofile%\AppData\Roaming\Skype\%SkypeName%\main.db
Windows XP: ROOT\Documents and Settings\%userprofile%\Application Data\Skype\%SkypeName%\
or RUN: AppData\Skype\%SkypeName%\
Linux: ~\.Skype\%SkypeName%\
Android: \data\data\com.skype.raider\databases\main.db
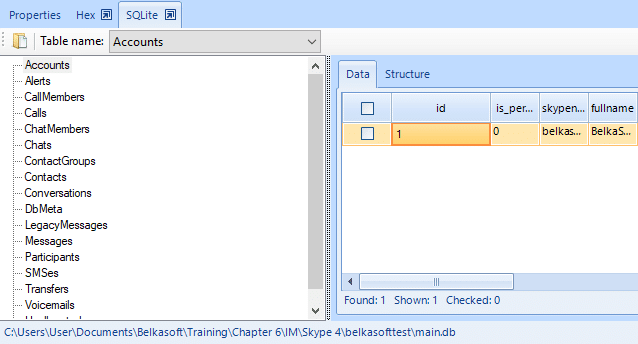
Displaying data of a main.db-file in SQLite viewer
Also, it is possible to restore some of the Chats from data files, which are temporary synchronization database files (ChatSynk).
The types of data that are contained in Skype and can be extracted:
- Calls
- Chats
- Group Chats
- SMS
- Voicemails
- File transfers
- Geolocation data
- Pictures
A complete list of data that can be extracted from Skype
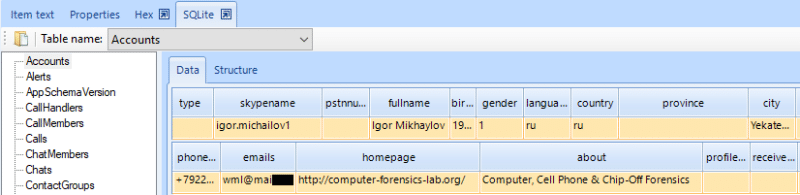
Accounts: the information about the user’s account can be obtained by analyzing the relevant fields of the main.db file in the SQLite Viewer.
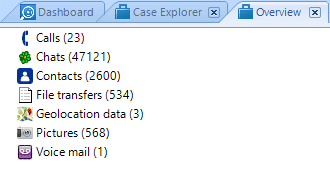
It is most convenient to navigate the extracted data in the Overview tab.
Chats
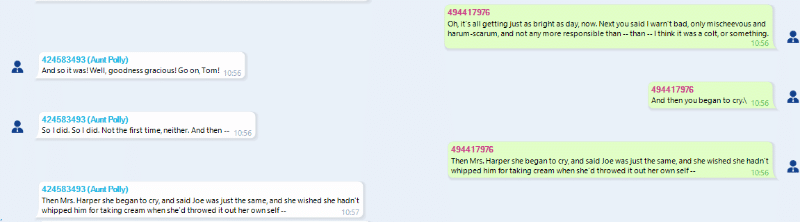
BEC automatically locates and extracts chat history from Skype database, as well as hundreds of other messengers
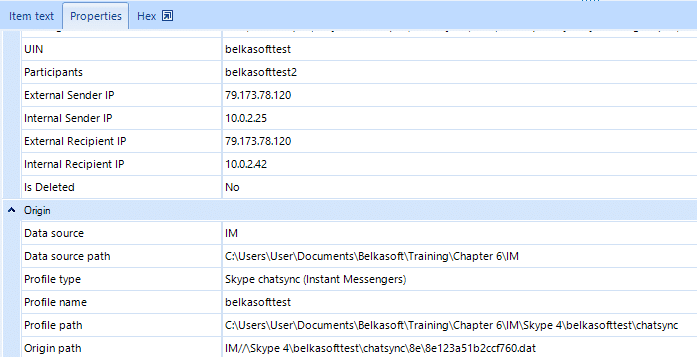
The window displays chat properties in the lower part of the window, where the following is indicated:
UIN of the sender and the recipient, External IPs and Internal IPs.
Calls: Voice calls made via Skype.

Contacts: Contents of Skype address book.
File transfers: Files sent and received via Skype.

Geolocation data: mobile Skype client allows a user to send their current location to an interlocutor. BEC extracts the data.
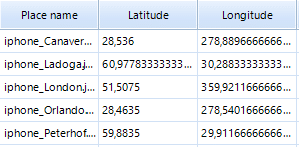
BEC can display extracted geotags on Google Maps.
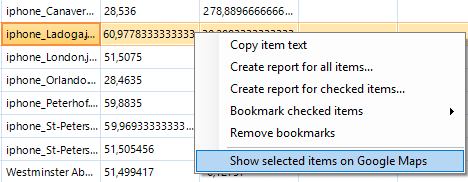
BEC can visualize one or multiple locations on Google Maps or Google Earth
Other artifacts: BEC can recover other artifacts of Skype. Such us: voicemails, group chats, etc.
Deleted chats
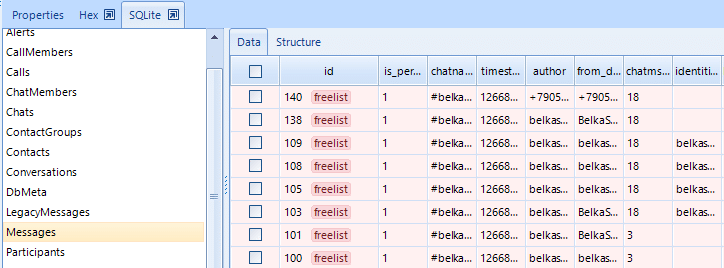
BEC can recover deleted records of Skype chats. BEC does this automatically. But, an examiner can do it in the manual mode, using SQLite viewer.
An SQLite database may have one or more unused pages. These pages be created and reserved for future use to improve performance, in which case they contain no meaningful data. Unused pages in the database are stored on what is called a “freelist”.
Freelist’s can contain remote chats and can be extracted manually or automatically.
A part of the deleted data can be in the Unallocated space area. For their restoration, an in-depth analysis is required.
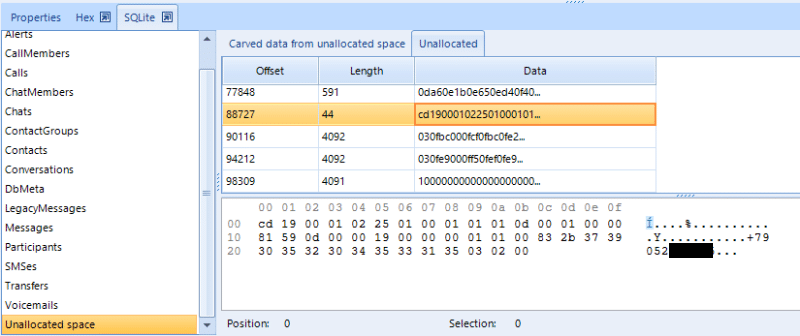
Phone number in Unallocated space
Write Ahead Logs
Another artifact from which you can extract Skype data is WAL-files. These files contain new and updated records and are used to ensure the integrity of the data when the content is updated of a main SQLite database. Data in WAL-files can be stored for a very long time. A WAL-file is cleared when it reaches the size of 1000-pages or when it receives a special command.
BEC also knows how to extract data from WAL-files automatically.
Conclusion
In this article, the functionality of Belkasoft Evidence Center for extracting Chats was reviewed. It was considered where the Chats are stored and from what objects the Chats can be extracted (computers, clouds, mobile devices, etc.).
With the example of Skype, it was shown what types of artifacts of Instant Messengers can be extracted and analyzed with the help of Belkasoft Evidence Center.
Happy forensicating!
About the authors
Oleg Skulkin, GCFA, MCFE, ACE, is a DFIR enthusional (enthusiast + professional), Windows Forensics Cookbook and Practical Mobile Forensics co-author.
Igor Mikhaylov, MCFE, EnCE, ACE, OSFCE, is a digital forensic examiner with more than 20 years of experience and Mobile Forensics Cookbook author.





