CorelDRAW is the best graphics editor, which is developed by a Canadian company Corel Corporation. This graphics editor has great functionality. Criminals can use it for illegal activities, such as fraud, money counterfeiting, etc. Today, we will describe how to detect CoralDRAW artefacts when examining a computer. We will use AXIOM by Magnet Forensics as a tool for analysis, which is one of the best tools for computer forensics.
Supported formats
The CoralDRAW program supports editing of many formats:
- Adobe Illustrator (AI)
- Font Printer Font Binary File – Adobe Type 1 (PFB)
- Windows Bitmap Image File (BMP)
- Raster Image OS/2 (BMP)
- Vector Graphics Format (CGM)
- CorelDRAW (CDR)
- Corel Presentation Exchange (CMX)
- Corel PHOTO-PAINT (CPT)
- Corel Symbols Library (CSL)
- Theme File Created by CursorXP (CUR)
- Microsoft Word (DOC, DOCX or RTF)
- Microsoft Publisher (PUB)
- Corel DESIGNER (DSF or DES)
- AutoCAD Drawing Exchange Format File (DXF)
- AutoCAD Drawing Database File (DWG)
- Encapsulated PostScript File (EPS)
- PostScript (PS or PRN)
- GIF
- HTML
- JPEG (JPG)
- JPEG 2000 (JP2)
- Image Kodak Photo-CD (PCD)
- PICT (PCT)
- Adobe Portable Document Format File (PDF)
- HPGL Plotter File (PLT)
- Portable Network Graphic (PNG)
- Adobe Photoshop (PSD)
- Corel Painter (RIF)
- Scalable Vector Graphics File (SVG)
- Macromedia Flash/Adobe Flash (SWF)
- Targa Graphic Image (TGA)
- Tagged Image File (TIF or TIFF)
- Corel Paint Shop Pro (PSP)
- Font TrueType (TTF)
- WordPerfect Document (WPD)
- WordPerfect Graphic File (WPG)
- Raw Images
- Wavelet Image (WI)
- Windows Metafile (WMF)
Using CorelDRAW you can edit any of the abovementioned types of formats, but, if CorelDRAW was used on the examined computer you will probably find files with the following extensions:
- .CDR is a file extension for vector images created in the design program – CorelDRAW. A CDR file contains a document that consists of text, lines, shapes, images, colors, and effects.
- .CPT is a file extension for bitmap images created in a photo-editing program developed by the Corel Corporation – Corel PHOTO-PAINT. This program is a part of the CorelDRAW Graphics Suite.
CorelDRAW metadata
Before starting an analysis, a forensic analyst wants to find information about the installed version of the CorelDraw program, such as date of installation, serial number, owner, etc.
This information can be found in the SOFTWARE file of the Registry, which is located on the following path: C:\Windows\System32\config\. Also, there is the easier way to do it: select the Registry option in the AXIOM drop-down menu.

Selection of the Registry option
In this part of AXIOM program, forensic analyst can navigate through all Registry elements of the examined operating system, such as SAM, SECURITY, SOFTWARE, SYSTEM and NTUSER.DAT. It is user-friendly and it speeds-up the working process.
Go to the path: SOFTWARE: Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\04137BC5C6086C240AA5A1DFE029ED5B\InstallProperties.
Here you can find the following CorelDRAW metadata:
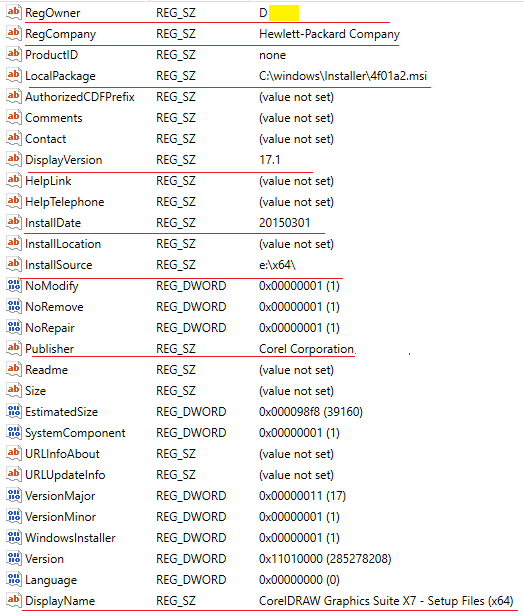
Values in the InstallProperties
Unfortunately, we could not find Serial Number in this part of the Registry.
Information from this part of the Registry is partially duplicated to SOFTWARE:Microsoft\Windows\CurrentVersion\Uninstall\
(Full paths:
Microsoft\Windows\CurrentVersion\Uninstall\{EF44BCCD-13F9-4974-862C-CCFAF43EE082}
Microsoft\Windows\CurrentVersion\Uninstall\{FC41DFBE-6C39-4C84-949B-7CB1E6460C7A}
Microsoft\Windows\CurrentVersion\Uninstall\{FC9BCB82-55E3-4328-868F-B19112B07B93})
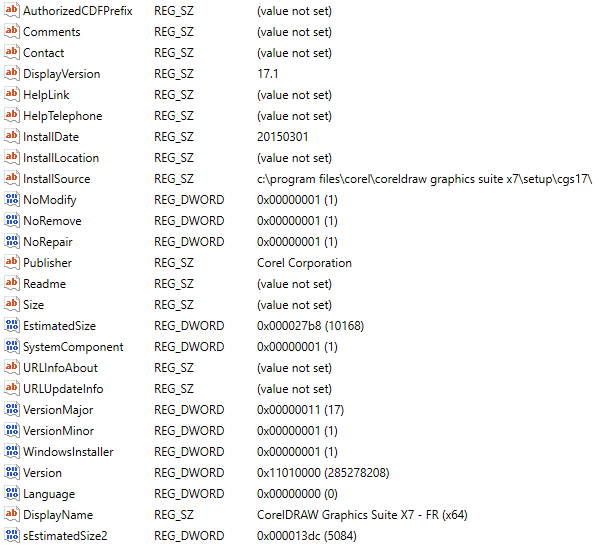
Values in Uninstall
Unfortunately, the Serial Number of the CorelDraw program was not found in this part of Registry either. Serial Number can be duplicated in the other elements of this tool. For example, Serial Number can be detected in the Registry of the CorelDRAW element – Corel Website Creator by the path SOFTWARE: WOW6432Node (full path: SOFTWARE: WOW6432Node\Corel\Website-Creator\13.5\).
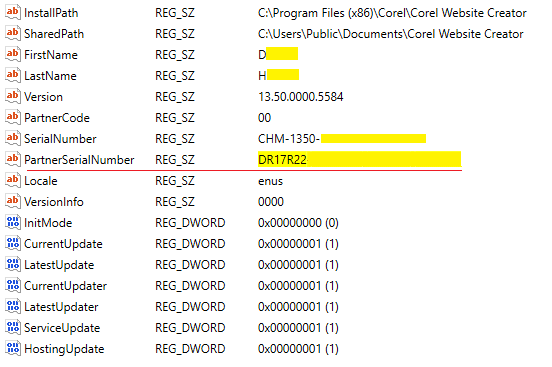
Values in WOW6432Node\Corel\Website-Creator\13.5\
Consequently, the analysis of the hive SOFTWARE provided us with the following data about the installed version of the CorelDRAW program:
- Owner: D…
- First Name (owner): D…
- Last Name (owner): H…
- Company: Hewlett-Packard Company
- Local Package: C:\windows\Installer\4f01a2.msi
- Display Version: 17.1
- Install Date: 03/01/2015
- Install Source: e:\x64\
- Publisher: Corel Corporation
- Display Name: CorelDRAW Graphics Suite X7 – Setup Files (x64)
- Serial Number: DR17R22-…
Is it a good result? It is a very good result.
Recent Files
The first thing that forensic analyst wants to know is what kind of files were edited via CorelDraw. The Resent files category is useful in this case.
In old versions of the CorelDRAW program, the Recent Files list is located in the CorelDraw.ini file (path: C:\Users\<username>\AppData\Roaming\Corel\<Product Name>\Draw\Workspace\<workspace name>\CorelDraw.ini (for example, Product Name: CorelDRAW Graphics Suite X5)).
In newer versions of the CorelDRAW program, this information is stored in the user hive NTUSER.DAT:
Software\Corel\CorelDRAW\<version>\Draw\Application Preferences\Framework:

The path to the Framework in the Registry
In the framework section, there is a list of files in the ResentFiles value that are divided with ‘|’ symbol. These files were opened and edited in the CorelDRAW program.
Unfortunately, this list does not contain timestamps, which means that forensic analyst will not be able to tell when these files were edited in the CorelDRAW program.
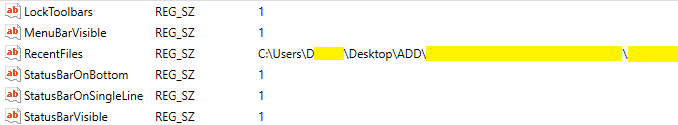
If these files are present on the examined hard drive, you can analyze their metadata in the file system and find out when they were accessed and edited. In order to do it you need to select File System option in the AXIOM drop-down menu. Go to the place where these CDR files are stored and check their metadata, such as Created, Accessed, Modified.
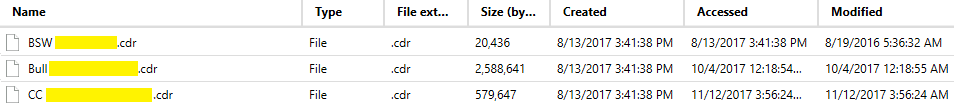
Other Activities
Other activities related with .CDR file can be detected by the analysis of LNK-files and Jump Lists.
Information goes to the LNK files when a user opens a file via Explorer.
Jump Lists provide a user with quick access to recently accessed application files.
In the AXIOM drop-down menu, select the Artifacts option. Enter .CDR in the filter window and then press the “GO” button.
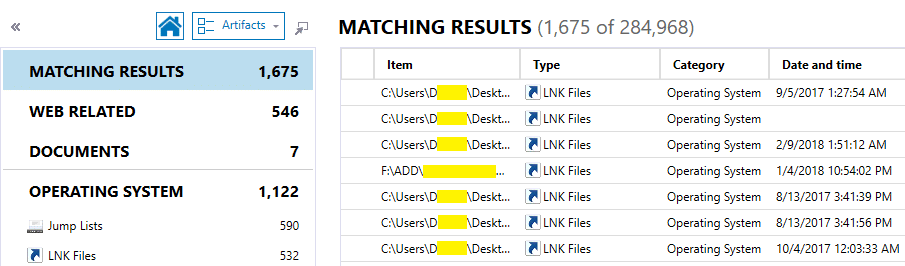
The result of the filter application.
As you can see from the picture above, the result of the filter application provides us with information that 590 Jump Lists artifacts and 532 LNK Files artifacts were found. These artifacts contain timestamps and can be used for the analysis of the intensity of the CorelDRAW program usage. We can make a timeline based on the timestamps of these artefacts. The timeline shows the intensity of the CorelDRAW program usage to the forensic analyst.
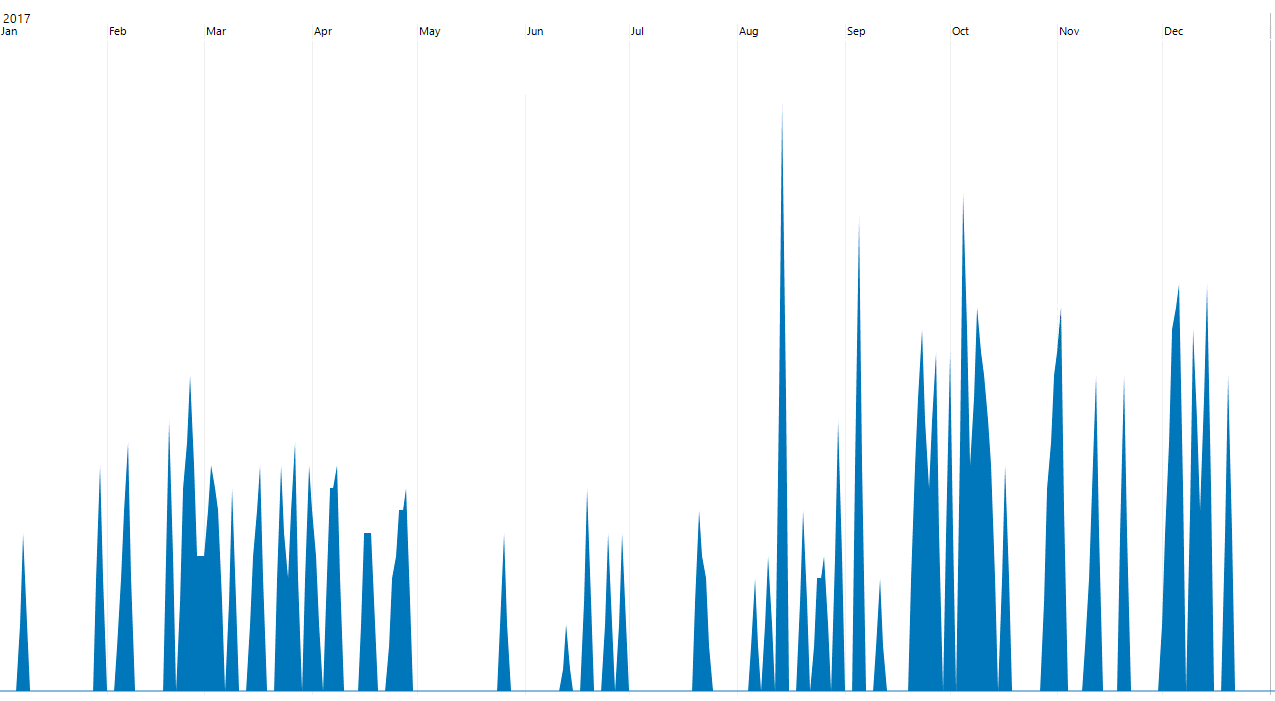
Timeline
You have definitely paid attention to the fact that some artefacts with .CDR extension were detected in the WEB RELATED category. Let us consider the detected artefacts more closely.

Web Related artifacts
Go to the Chrome Downloads category and check what data are presented there.
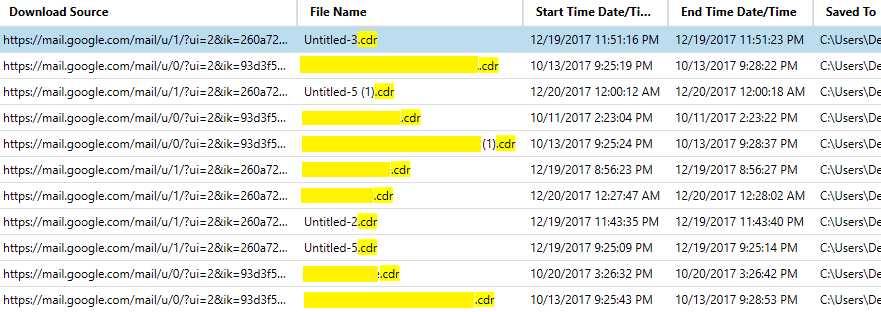
Chrome Downloads artifacts
As you can see from the picture above, part of CDR files was downloaded from Internet using Gmail account.
Conclusion
In this article we have described how to detect metadata of the installed version of the CorelDRAW program (such as date of installation, activation key, owner, etc.), based on the analysis of the Windows Registry. Also, we have described how to find recent files and find out their timestamps; how to detect other activities on the examined computer that are related with opened and edited files via CorelDRAW. In addition, we have shown how to detect the source of the files origin that can contain information relevant to the case (in the presented example, a part of files was downloaded to the computer using Gmail account).
As a tool for analysis, we used the forensic tool – AXIOM, which allows to perform the described process of analysis in a convenient and functional interface from the very beginning till the end.
Happy forensicating!
About the authors
Oleg Skulkin, GCFA, MCFE, ACE, is a DFIR enthusional (enthusiast + professional), Windows Forensics Cookbook and Practical Mobile Forensics co-author.
Igor Mikhaylov, MCFE, EnCE, ACE, OSFCE, is a digital forensic examiner with more than 20 years of experience and Mobile Forensics Cookbook author.






Comments are closed.