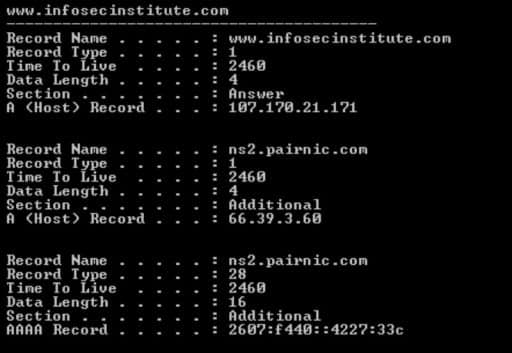
It is not that interesting – DNS process, DNS search, DNS reverse lookup, transfer of DNS-zone? This article examines the entire process, as well as some tools to analyze and enumerate DNS-traffic.
Domain Name System (DNS) is a naming system used to convert human readable domain names like infosecinstitute.com into a numerical IP address. DNS removes the IP-address for the requested domain. DNS settings can be controlled in the end user’s system. With the work of DNS sure sign everyone, but brush up on your knowledge here.
Kali distro is specially assembled for pen testers and have some really cool tools available to do pen-test in just a few clicks. For DNS analysis also it has some great tools such as:
1. Dnsenum
2. Dnsrecon
3. Dnstracer
Many of you are already familiar with a tool like Wireshark. It is a powerful tool and is an extremely popular tool mainly because it supports a wide protocol and user-friendly interface. Wireshark works with the vast majority of known protocols, has a clear and logical GUI. DNS traffic analysis adds a lot of context in the course of the investigation, for example, you can create indicators of compromise on the basis of DNS-traffic, we can detect the transfer of DNS zones, and even the organization can look at how much information he actually discovered about yourself.