Nowadays every digital forensic examiner knows that volatile data may contain lots of case relevant evidence. Such data may include such important information as remnants of different chats, webmail activities, running malware and even decryption keys for encrypted volumes.
There are a number of tools on the market capable of creating live RAM dumps, but today we are going to show you how to create a memory dump with Live RAM Capturer – a free tool developed by Belkasoft.
Let’s start. Download the tool using this link and put it to a USB flash drive. There are two versions of the product – 32-bit and 64-bit. We recommend you to have both on your drive. Choosing the right one depends on the target system.
Start the tool. You’ll see the following window:
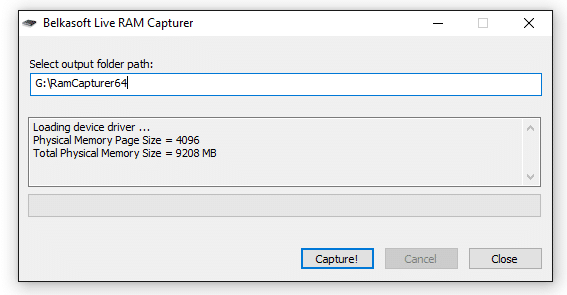
As you can see, the driver is successfully loaded and we see physical memory page size (4096) and total physical memory size. Before starting the capture make sure there is enough free space on your flash drive. After that press “Capture!” button.
Then capturing is finished, you’ll see a new line: “Memory dump completed. Total memory dumped = *** MB”. In our case it’s 9208:
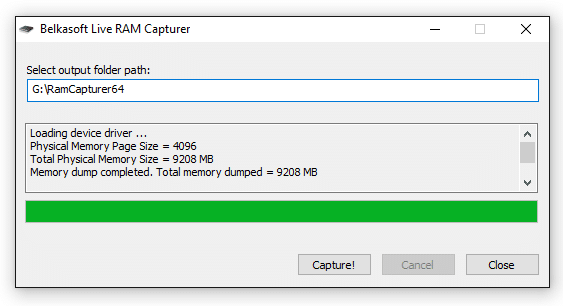
And that’s the total physical memory size! That’s it. We have captured the whole physical memory. Now we have a file with “mem” extension on our USB drive ready to be analysed with your favorite piece of digital forensic software. We usually use Belkasoft Evidence Center for memory dumps analysis.
It’s important to note that Live RAM Capturer complies all the forensic requirements of memory capturing: it operates in kernel mode, leaves the smallest footprint possible, it’s portable and uses read-only access.






