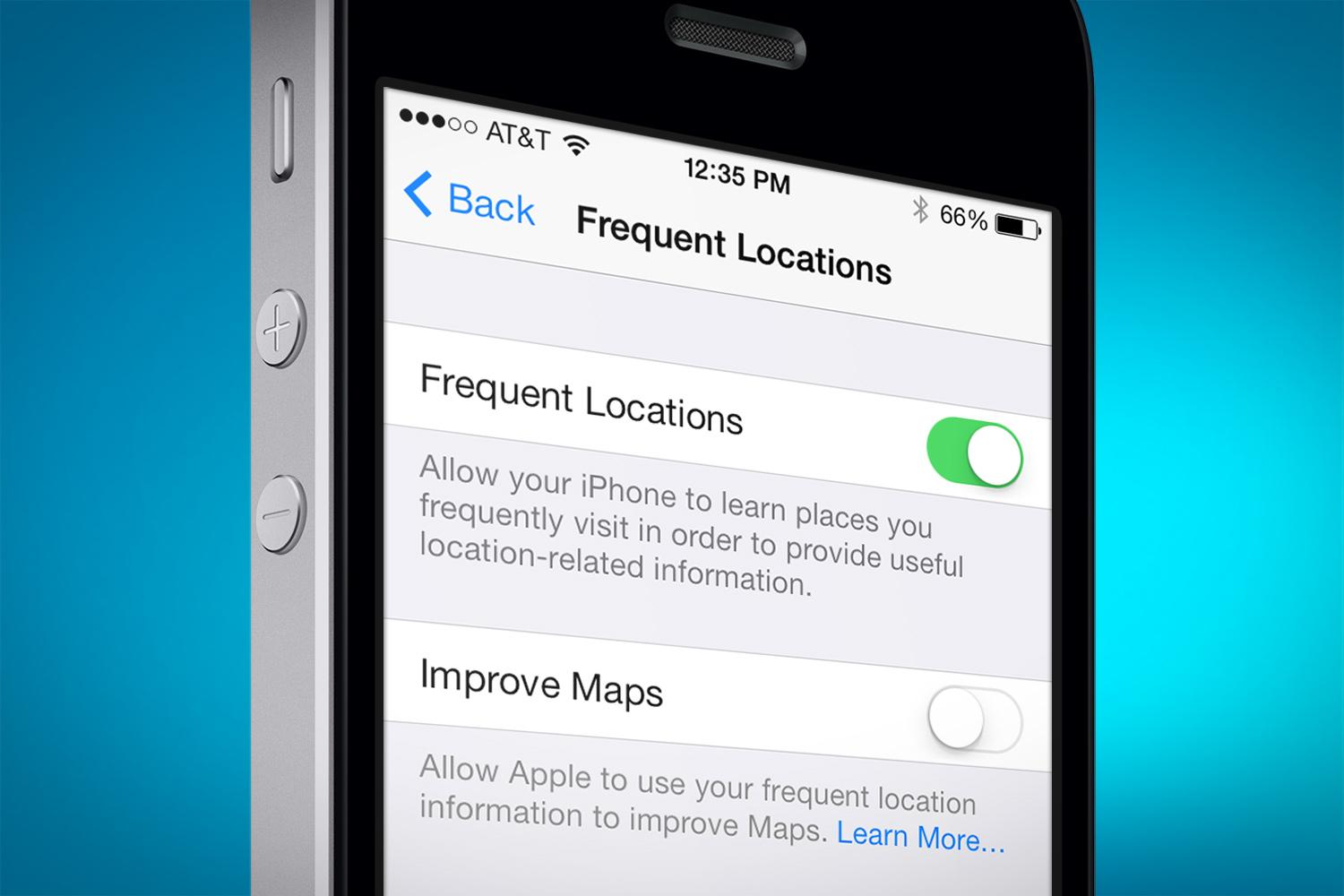
“Frequent Locations” are going to be a forensic goldmine in lots of cases. Parsing the artifacts can help an investigator to find locations the device has been. The “Frequent Locations” feature was introduced with iOS 7 release. It is enabled by default.
According to Sarah Edwards’ research, it’s data is stored in two binary plists under /private/var/mobile/Library/Caches/com.apple.routined/. You can access the files only if you a physical dump or physical access to a device (jailbroken device).
To make our lives easier, Sarah has written a python script that parses these plists.
It has two dependences: hexdump.py and ccl_bplist.py. Both files can be put to the same folder as the script. The script can be downloaded here.
The script is really easy to use:
python dump_freq_locs.py StateModel1.archive > StateModel1_parsed.txt
Again, more info about “Frequent Locations” forensics you can find here.






Comments are closed.