Alissa Torres is a certified instructor with SANS and the co-author/instructor of FOR526: Memory Forensics In-Depth.
She has extensive experience in information security, spanning government, academic, and corporate environments.
In the forensics world, the hunting of evil never ends. And with Windows 10 expected to be the new normal, digital forensics and incident response (DFIR) professionals who lack the necessary (memory) hunting skills will pay the price.
Investigators who do not look at volatile memory are leaving evidence at the crime scene. RAM content holds evidence of user actions, as well as evil processes and furtive behaviors implemented by malicious code.
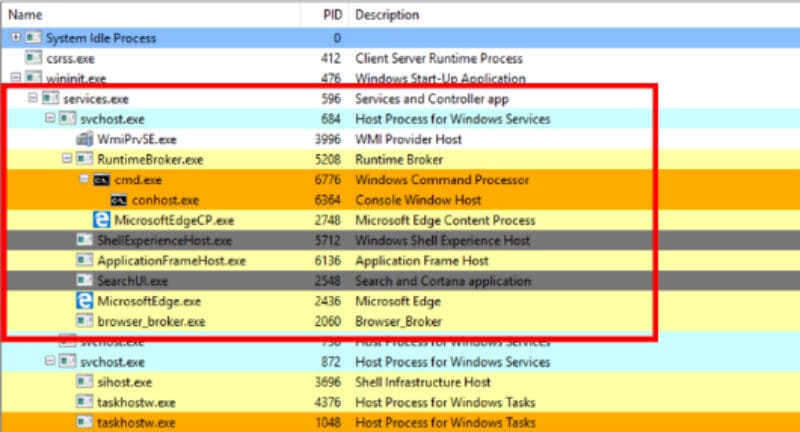
In performing memory analysis, an investigator must understand the normal parent-child hierarchical relationships of native Windows processes. This hierarchical process relationship deviates from one of the traditional analysis techniques
An example of network activity from the SearchUI process is shown here.
The memory data compression behavior first seen in Windows apps on Windows 8 has been implemented on a wider scale in Windows 10. Now when the memory manager detects “memory pressure”, meaning there is limited availability for data to be written to physical memory, data is compressed and written to the page file. With the implementation of Windows 10 memory compression, a new obstacle exists for such analysis.
With so many different features added between Windows versions as well as significant changes rolled out in updates, having a tool that uses the publicly available Windows symbols, like Rekall, is key. When profiles have to be created in order to support new versions of Windows as seen in analysis tools, there is lag time. Rekall automatically detects the Windows version. Because it is often difficult to discern what version of Windows 10 your target system was running at the time memory was acquired.
A recap on how things have changed in recent versions of Windows will speed your analysis.