Today, the military and security officers need immediate access and the ability to gather information from computers, smart phones, tablet PCs and other digital devices. However, the biggest problem today is the complex software, large and heavy hardware and time-consuming process of collecting and analyzing information.
Advanced Digital Forensic Solutions, Inc. (ADF Solutions, Inc., or ADF Solutions) is a privately held company that was founded in 2005 by JJ Wallia and Rafael Bousquet.
ADF Solutions develops tools for the exploitation of the media (MEDEX) and digital grading forensics. These tools scan computers and digital devices and quickly extract intelligence and evidence to identify individuals who pose a threat to public safety or national security. They are used in digital laboratories forensic – medical and used in the field operatives in the defense, intelligence, law enforcement, border security and other government agencies around the world.
ADF Solutions has developed a Triage -G2 to comprehensively address the problem. This tool is used in the US Department of Defense.
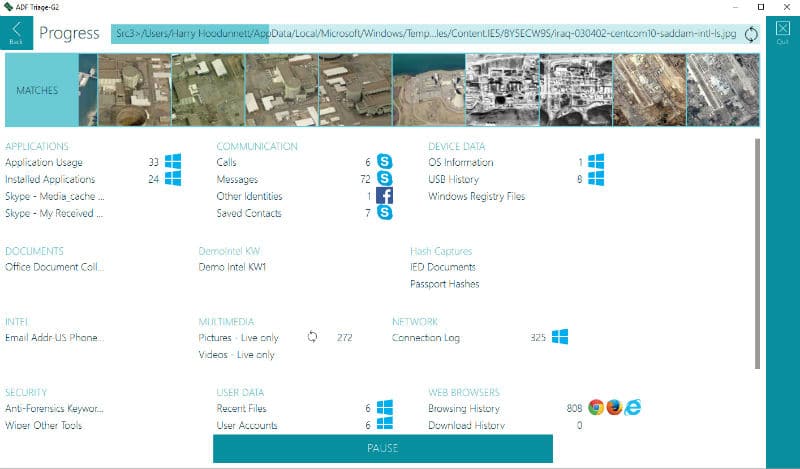
Triage-G2 is designed specifically for use by untrained staff. A deployment in the field does not require any computer, but only Triage Key (USB flash drive). Triage Key may be pre-programmed to search, or a specific one of the multiple search criteria at the base under investigation can be selected in the computer field. Thereafter Traige Key automatically collects the files on the specified criteria. The collected data can be viewed immediately on the test computer, or later in the forensic lab for deeper analysis.
The powerful engine to search for can be configured to find the information on the certain conditions, the hash value. Triage-G2 can collect extensive information on the system, including data on the Internet searching and browsing history, browser history log using a USB device, the most commonly used applications and more.
It is equally important that the main features Triage-G2 include:
• Extreme ease of use, with minimum training required (one-half to one day).
• Portable, lightweight deployment utilizing a rugged USB key
• Immediate identification and analysis of actionable intelligence by leveraging highly scalable watch lists
• Easy ingestion of collected data into other data repositories.
• Automatic production and collation of intelligence reports.
• Powerful booting (including UEFI secure boot and Macs), providing access to internal storage that cannot easily be removed.
• Both forensically sound and stealth mode (to support covert operations) capabilities.