In the era of mobile technology creates a lot of mobile applications, both useful and harmful.
The types of malware are developing very quickly, which cause damage.
Manual malware analysis has always been a slow process – taking days and even weeks per sample – rendering the task impractical even for a small sample pool.
Many researchers malware has long wanted to create a system that will accept the application and prepare a report describing exactly what it was doing when it started, specifically pointing to something “suspicious” that allows us to carry out an initial analysis, without human intervention.
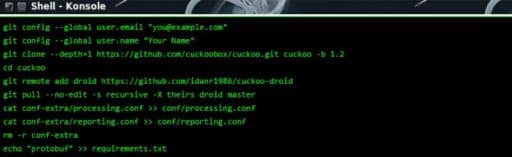
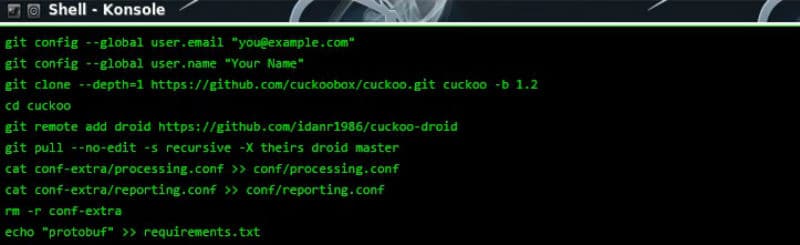
Idan Ofer Revivo and Kaspi of the research team at Check Point malware created CuckooDroid application.
CuckooDroid is an extension of Cuckoo Sandbox the Open Source software for automating analysis of suspicious files, CuckooDroid brigs to cuckoo the capabilities of execution and analysis of android application.
CuckooDroid: an automated, cross-platform, emulation and analysis framework based on the popular Cuckoo sandbox and several other open source projects – providing both static and dynamic APK inspection, as well as evading certain VM-detection techniques, encryption key extraction, SSL inspection, API call trace, basic behavioral signatures and many other features. The framework is highly customizable and extensible – leveraging the power of the large existing Cuckoo community.
The developers of the program believe that the fight against the growing threat of Android malware has to be an industry-wide effort – so CuckooDroid can used everybody.
You can find more info about CuckooDroid here.