Cybersecurity
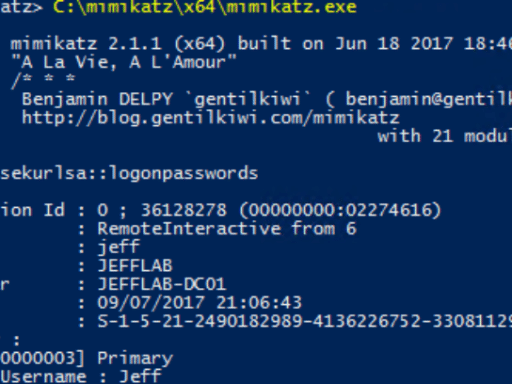
Cybersecurity is the practice of protecting systems, networks, and data from digital threats. In the context of digital forensics and cyber investigations, it involves defending against cyberattacks, identifying vulnerabilities, and responding to security breaches. Experts in this field analyze incidents, mitigate risks, and develop strategies to safeguard against evolving cyber threats, ensuring data integrity and confidentiality.
360 posts