In 34th episode of the Digital Forensic Survival Podcast Michael Leclair talks about his favourite tools for OS X forensics. He presents a wide list of forensic tools, which can be used for solving common problems, such as imaging, file analysis, data carving, decryption, email analysis, etc. Here is the full list of tools discussed in the podcast:
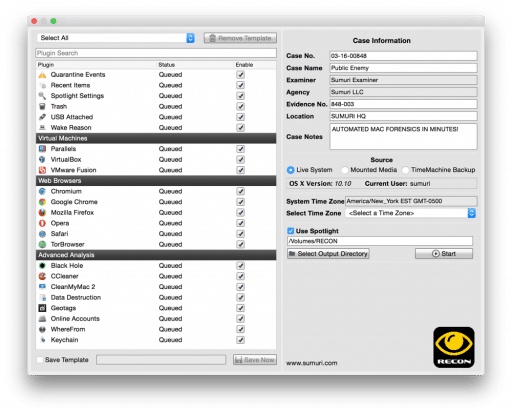
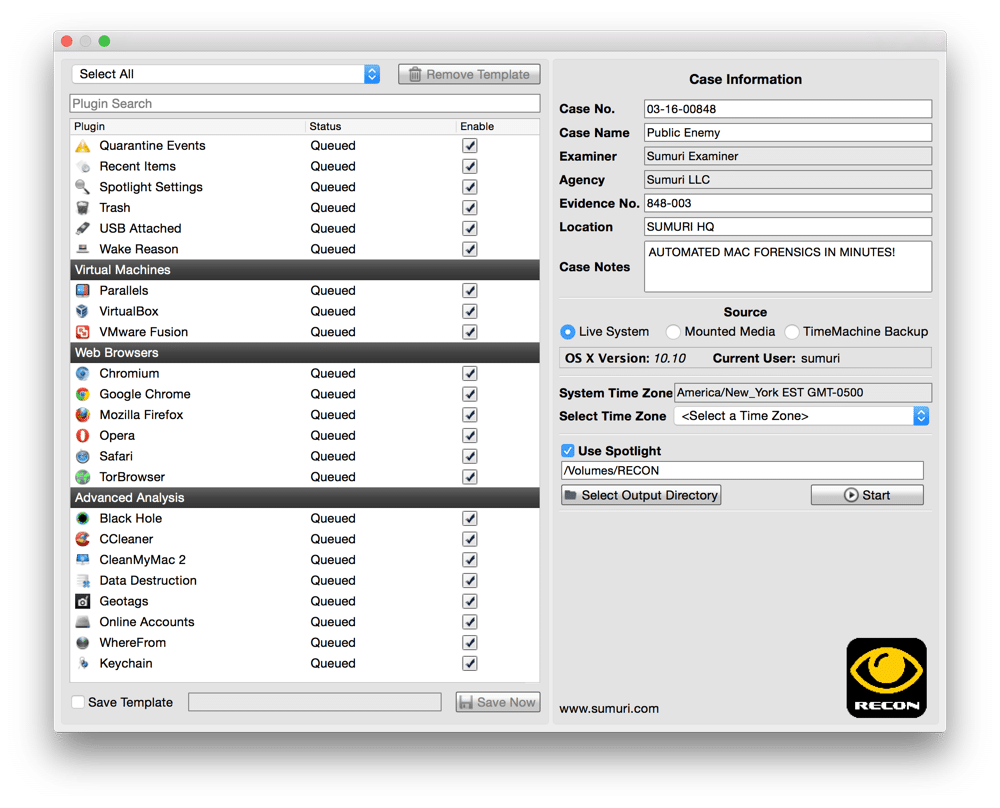
RECON for Mac OS X – Automated Mac Forensics, RAM Imaging, Search features, Live Imaging and Timeline generation.
PALADIN – Free imaging option. Offers remote imaging feature where client boots system and examiner can access to complete imaging tasks. You can use it for Fusion drives though you have to reassemble in terminal afterwards.
File XRAY – Low level file explorer.
DCFLDD – for imaging in Terminal.
File Juicer – automated datacarving.
Xcode – free from Apple, OS X add-on.
SQLITE Database Browser – Firefox has a plugin that works well (off line).
PLIST Editor Pro
Stellar Phoenix Data recovery tools – one of the best I have found for comprehensive data recovery, resurrecting formatted volumes, etc.
PASSWARE – for attacking Filevault2 protected volumes and Keychains.
EXIFTOOL – metadata parser.
iBored – hex editor.
EASY FIND – Another option for searching mounted DMGs on a Mac that offers options Spotlight does not.
Emailchemy – Email converter.
MacFuse
NTFS for Mac